SSO Authorization
1. Introduction
In Appcircle, authorization for SSO users is managed by mapping user roles and groups from your identity provider (IdP) to specific module permissions within Appcircle. This ensures seamless Role-Based Access Control (RBAC) across the platform.
Before configuring SSO-based authorization, you must first complete the SSO integration setup. You can refer to the SSO Integration Documentation for detailed instructions on how to configure SSO with your chosen provider, such as Keycloak, Azure AD, Okta, or Auth0.
Once SSO integration is complete, you can configure authorization by mapping IdP roles and groups to Appcircle module permissions.
Prerequisites
- SSO integration with your chosen identity provider (Auth0, Azure AD, Okta, OneLogin, Keycloak).
- Knowledge of groups and roles in your IdP that you want to map to Appcircle permissions.
- Administrative access to Appcircle and your IdP.
2. General Configuration Steps
These steps will guide you through the configuration within your chosen identity provider and Appcircle.
Step 1: Configure Your Identity Provider
- Perform identity provider-specific configurations, including creating groups and roles, and defining group and role claims/attributes.
- In Appcircle, enter the group and role claim/attribute names as defined in your IdP.
Follow 3. Specific Provider Configuration section to complete this steps.
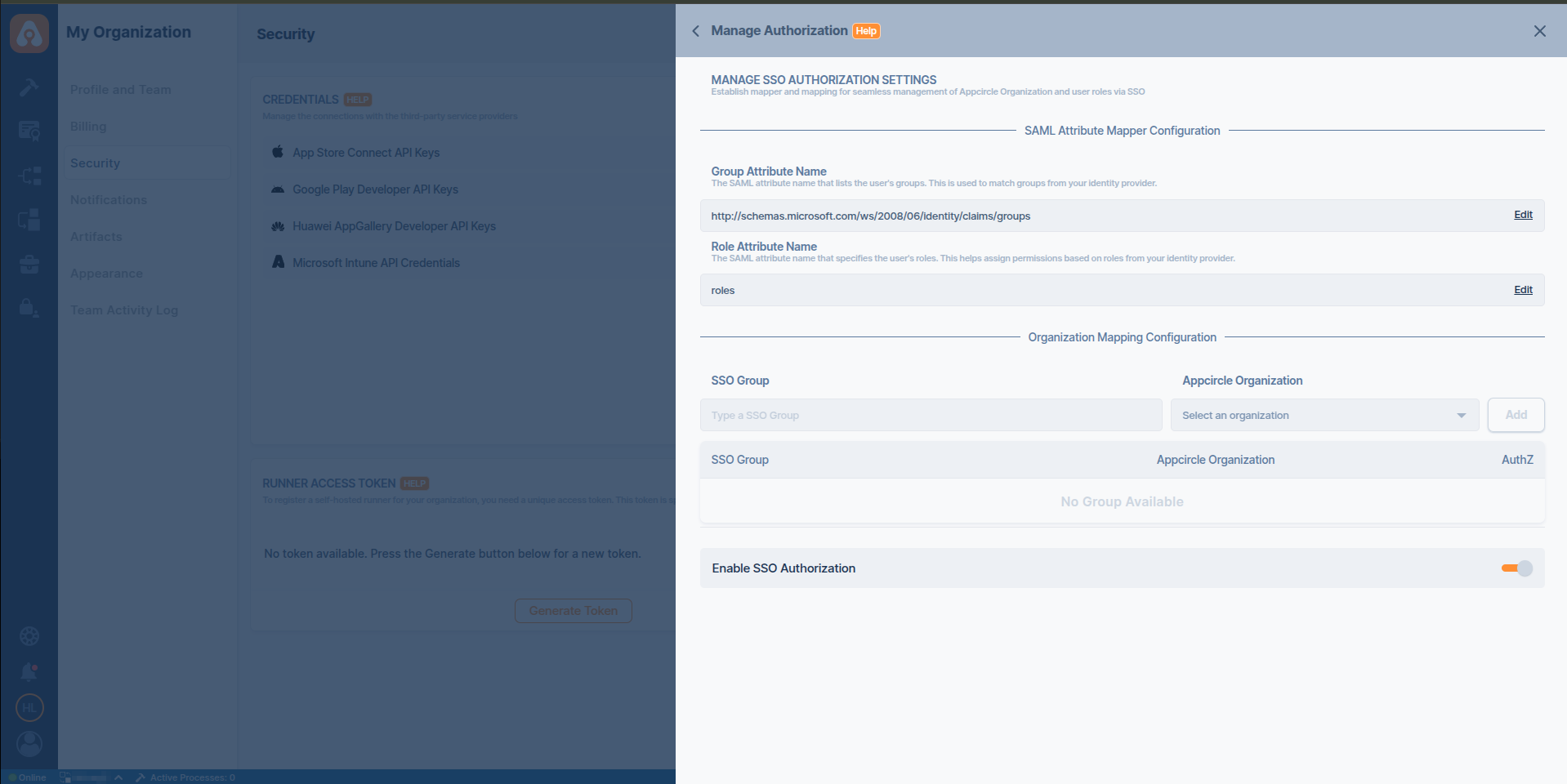
Step 2: Enable SSO Mapping and Configure Group and Role Mappings
Accessing SSO Mapping Settings
- Navigate to the Organization section on your dashboard.
- Select the Integrations and click on the Appcircle Login.
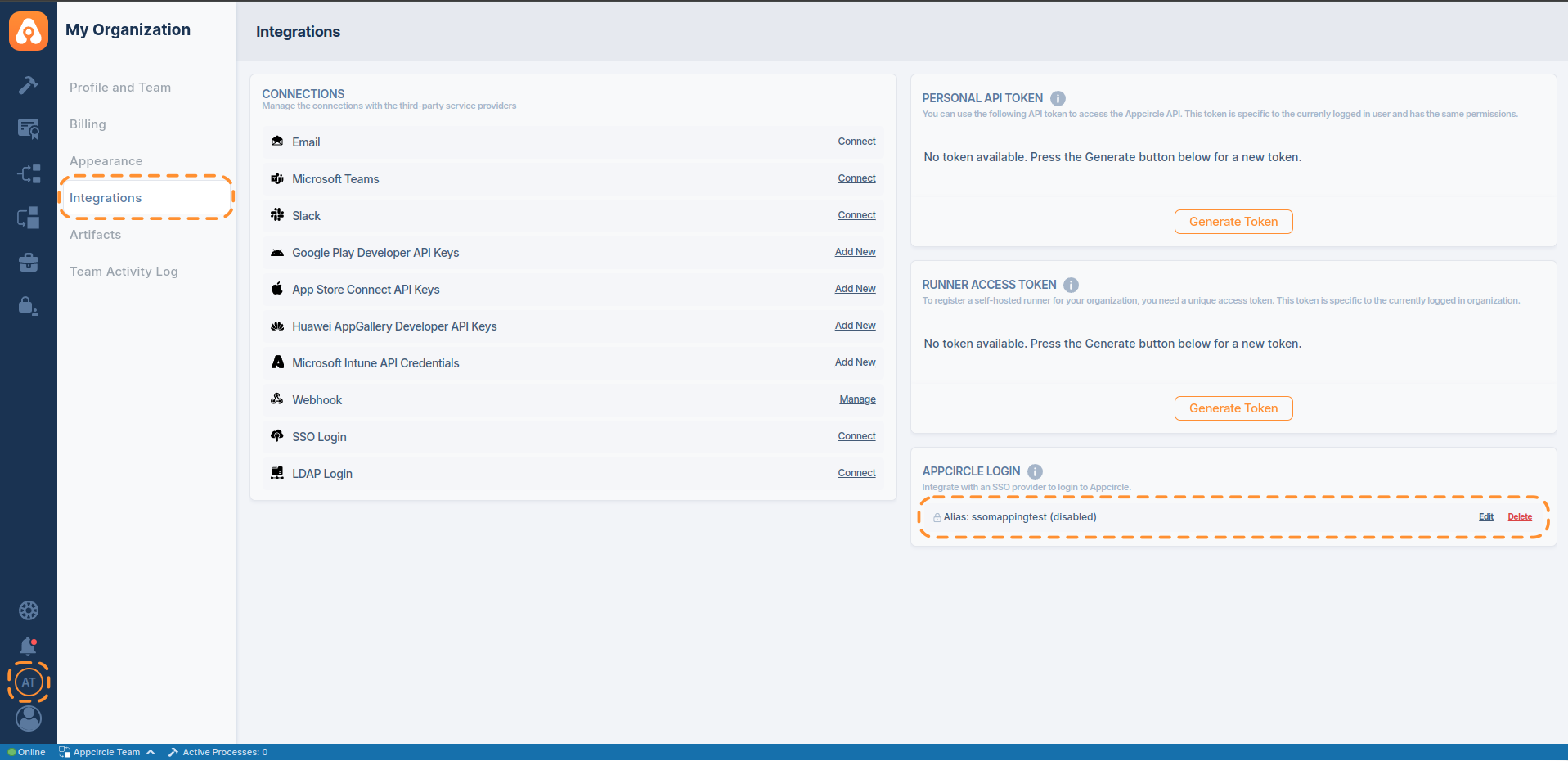
- Enable SSO Mapping and click Configure .
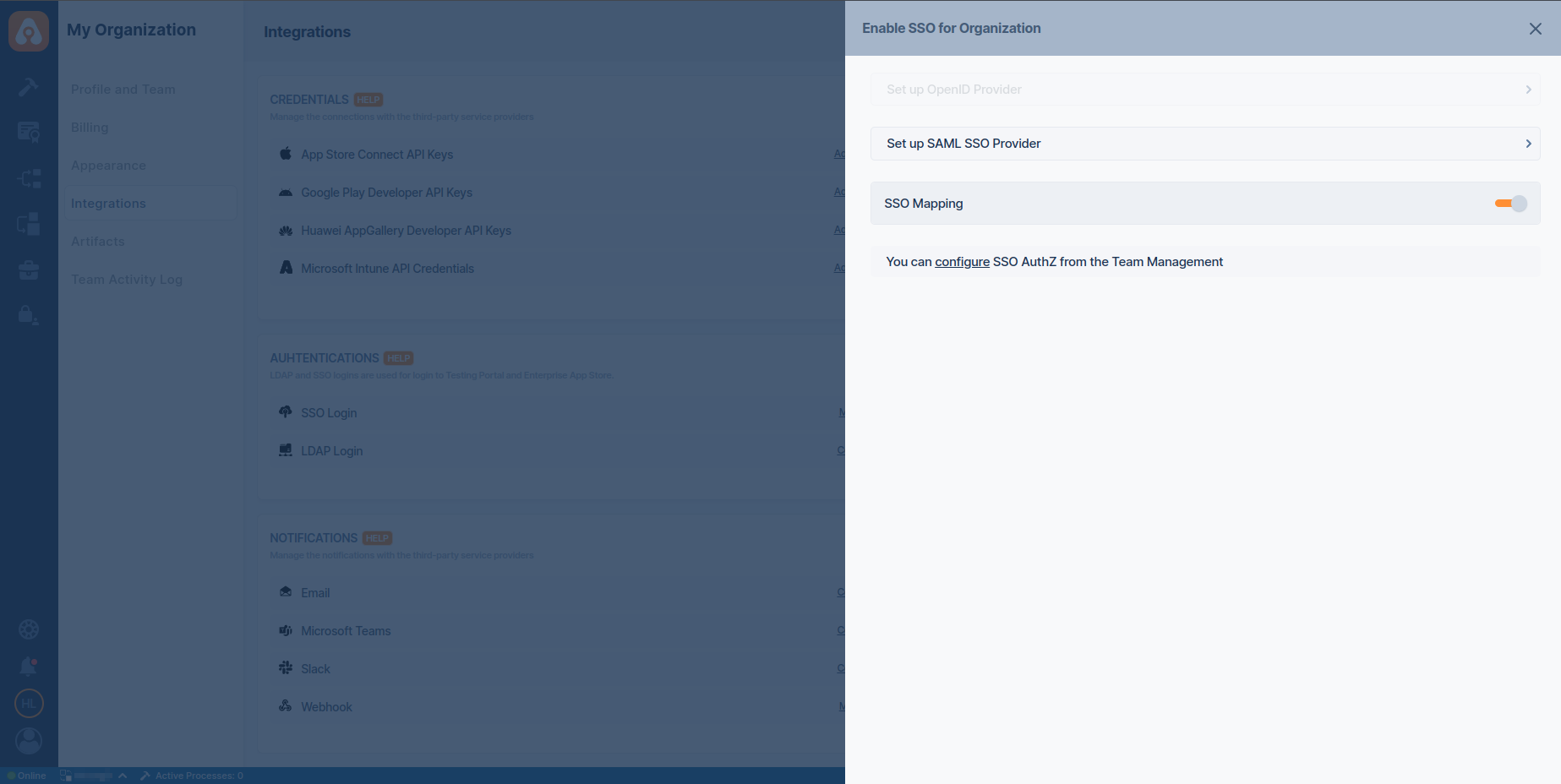
Group and Role Mapping Configuration
-
Enter the name of the SSO group and select the corresponding Appcircle organization you want to map. Ensure the group name is correct.
-
Click Add to map the SSO group to an Appcircle organization. This will automatically link users from the SSO group to the selected organization in Appcircle.
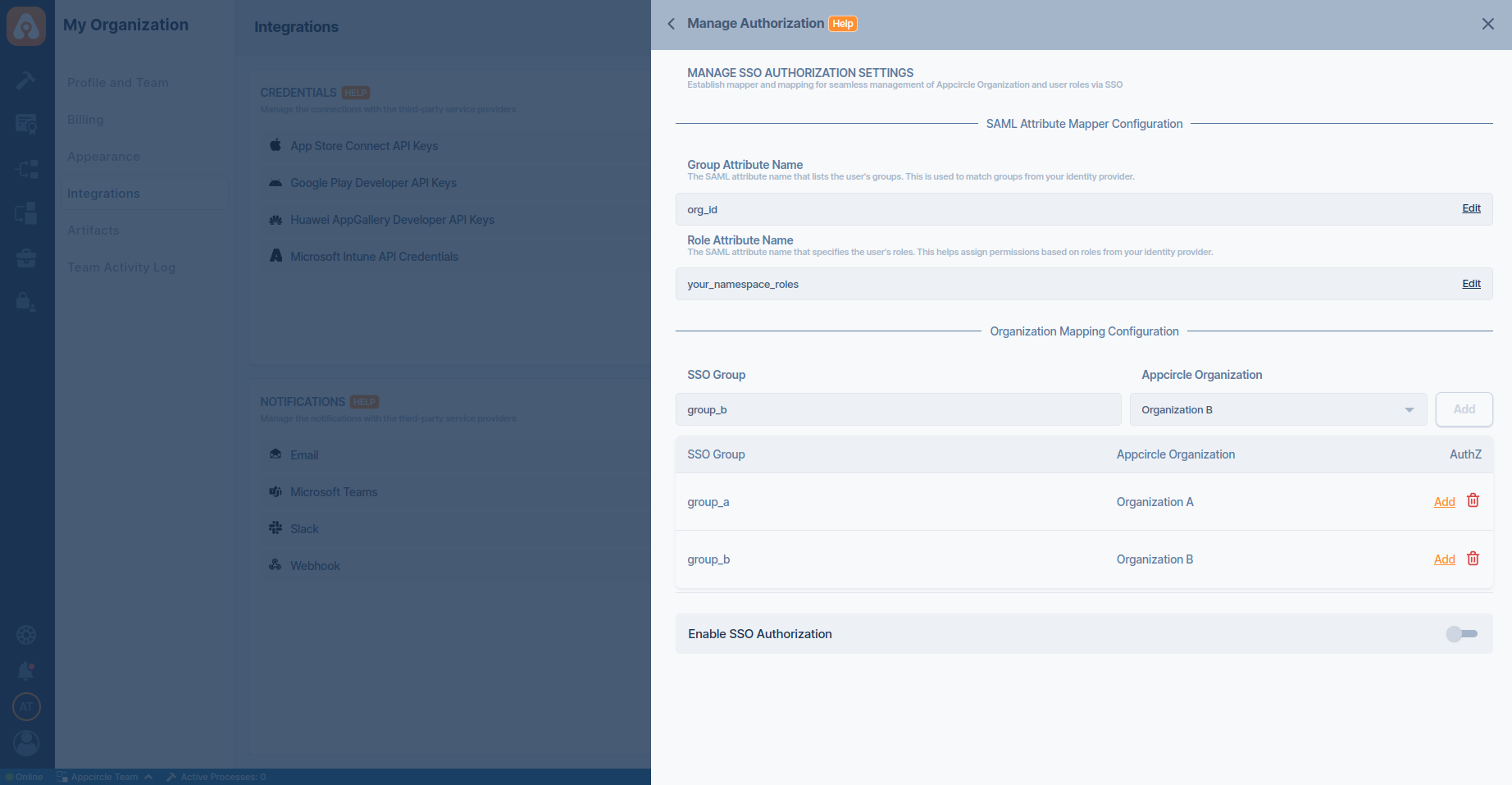
- You can define role mappings for each group mapping. Click the Configure button to set up role mappings.
- Enter the role name and select the corresponding Appcircle roles you want to map. Ensure the role name is correct.
3. Specific Provider Configuration
Auth0
Auth0 (OpenID Connect)
Step 1. Create Roles
- In the Auth0 dashboard, navigate to the User Management > Roles section.
- Click Create Role button. Create necessary roles.
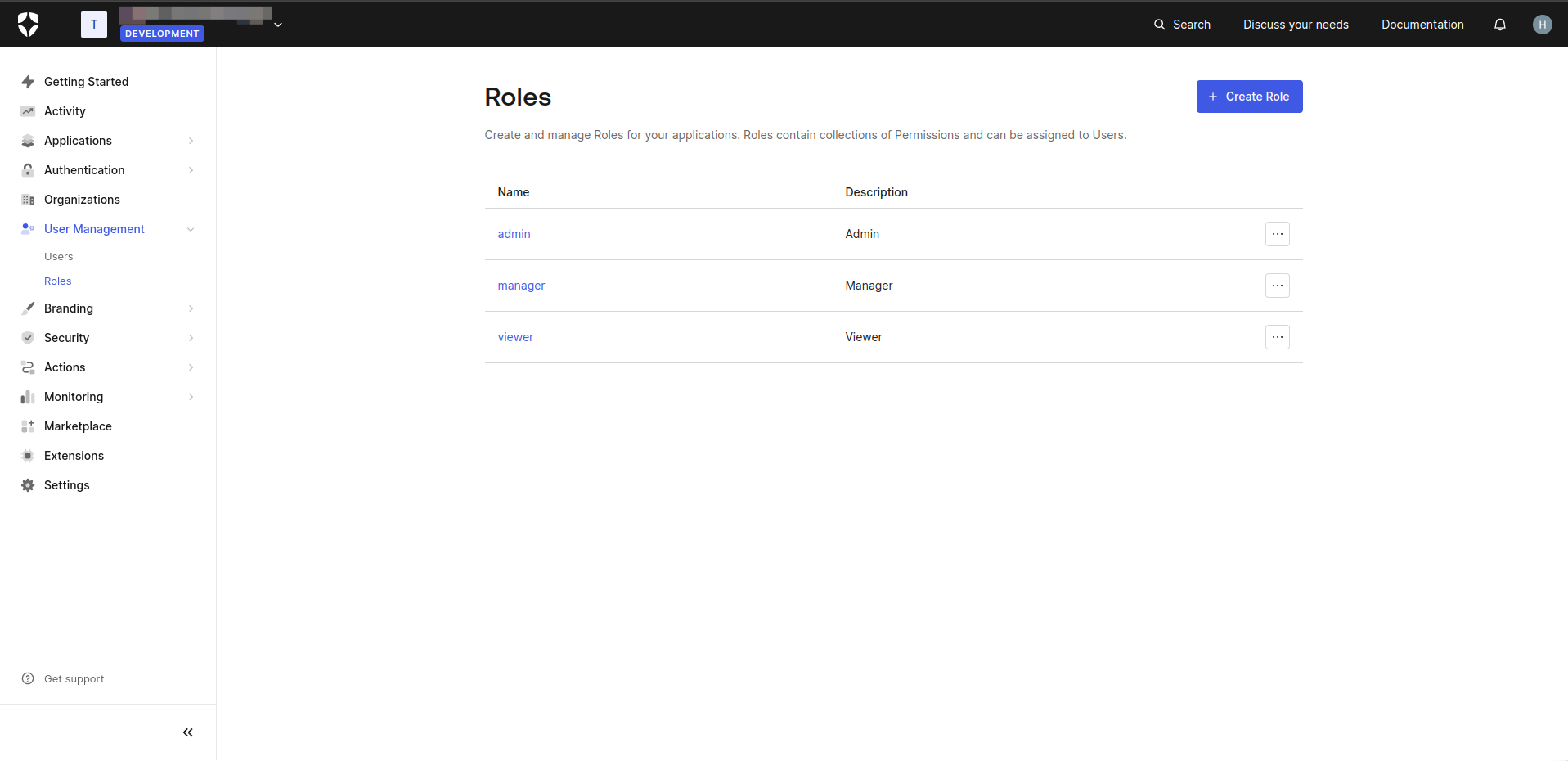
Step 2. Create Organization
- In the Auth0 dashboard, navigate to the Organization section.
- Click Create Organization button to create organizations.
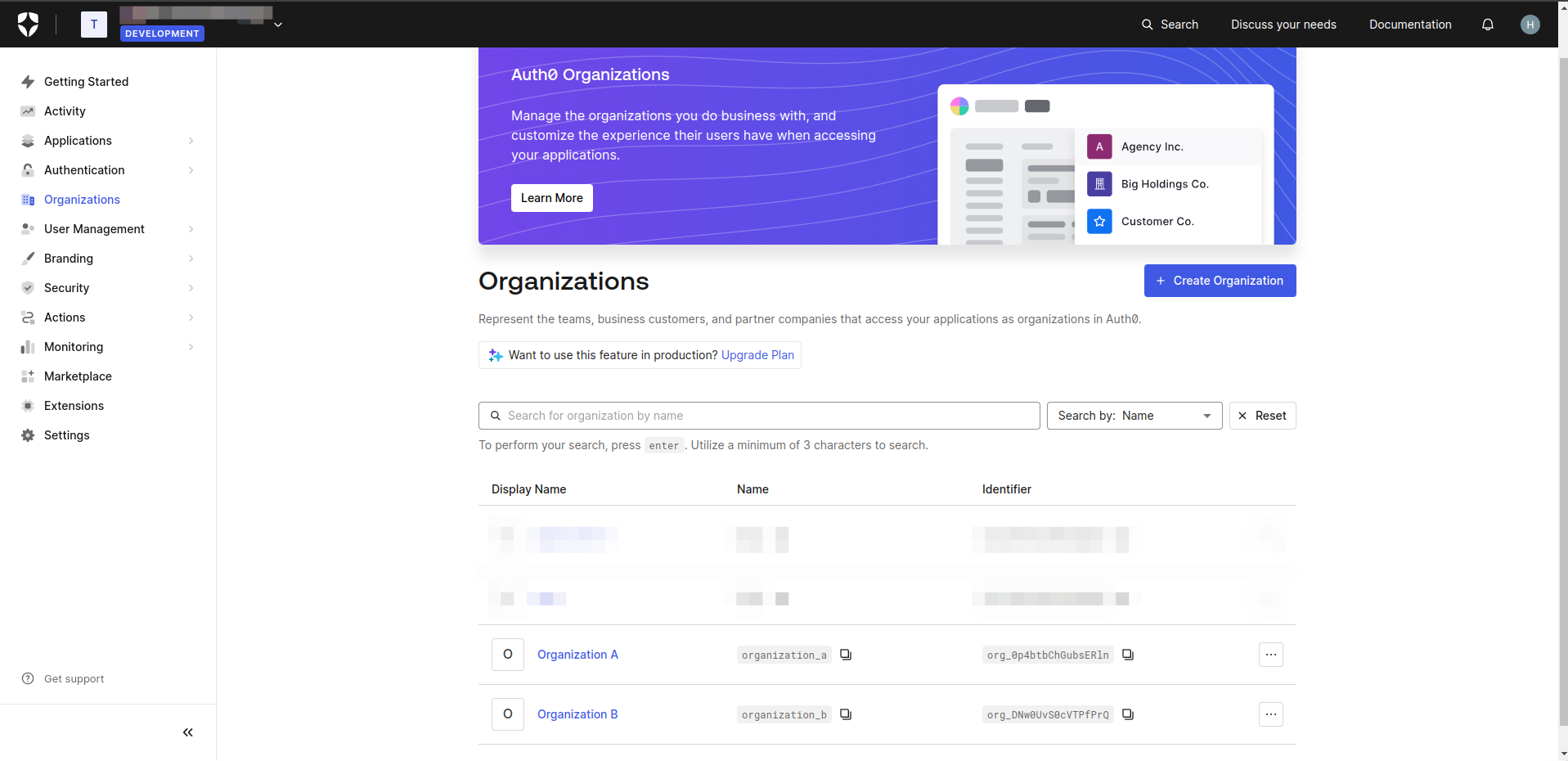
- Click the created organization to navigate to Organization Details.
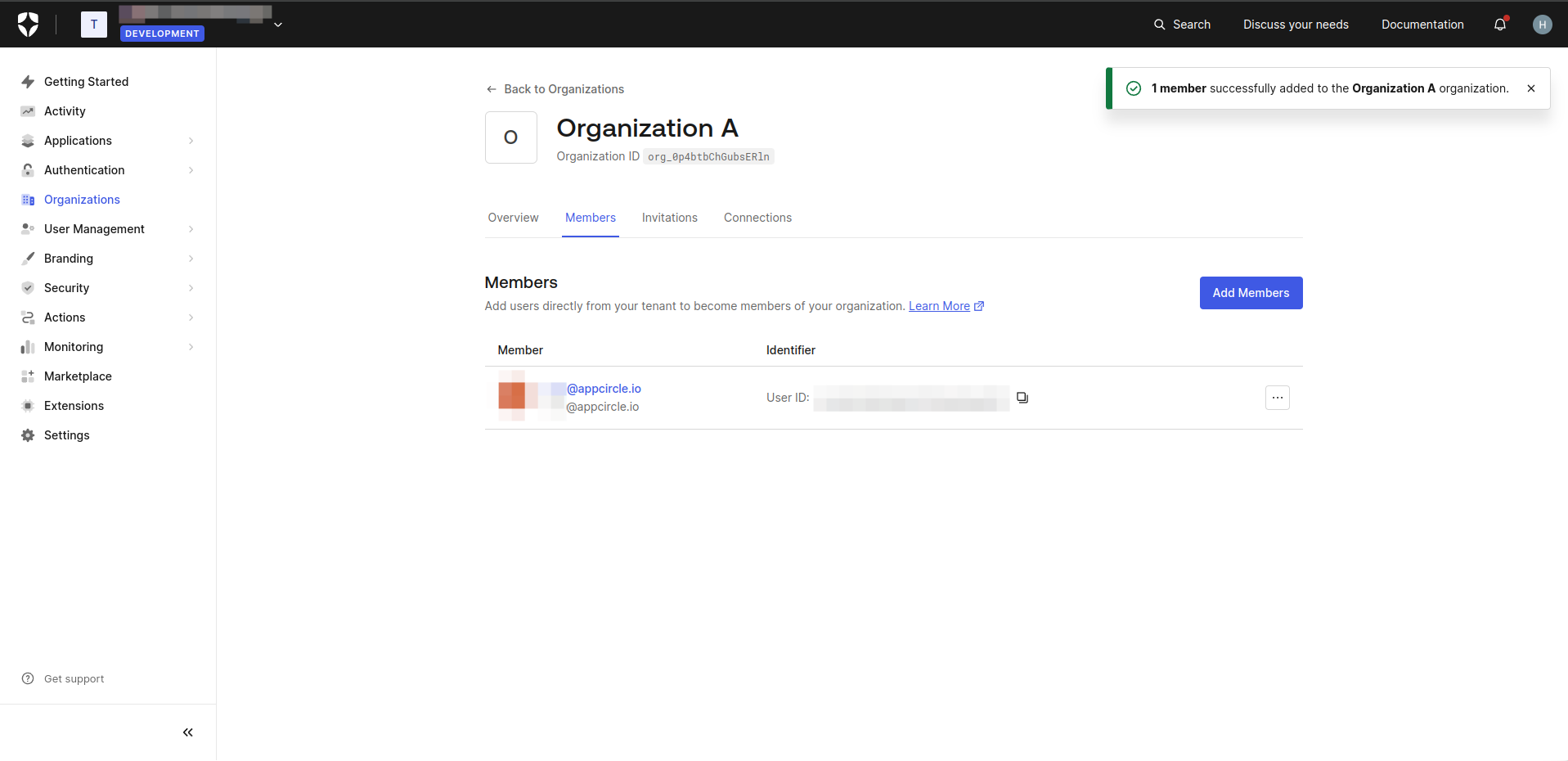
- On the Organization Details screen, click the Members tab to manage members of organization.
- Click the Add Members button to add users who will become members of your organization.
- On the Members screen, click the three dots and select Assign Roles. Assign the desired roles to users for organization.
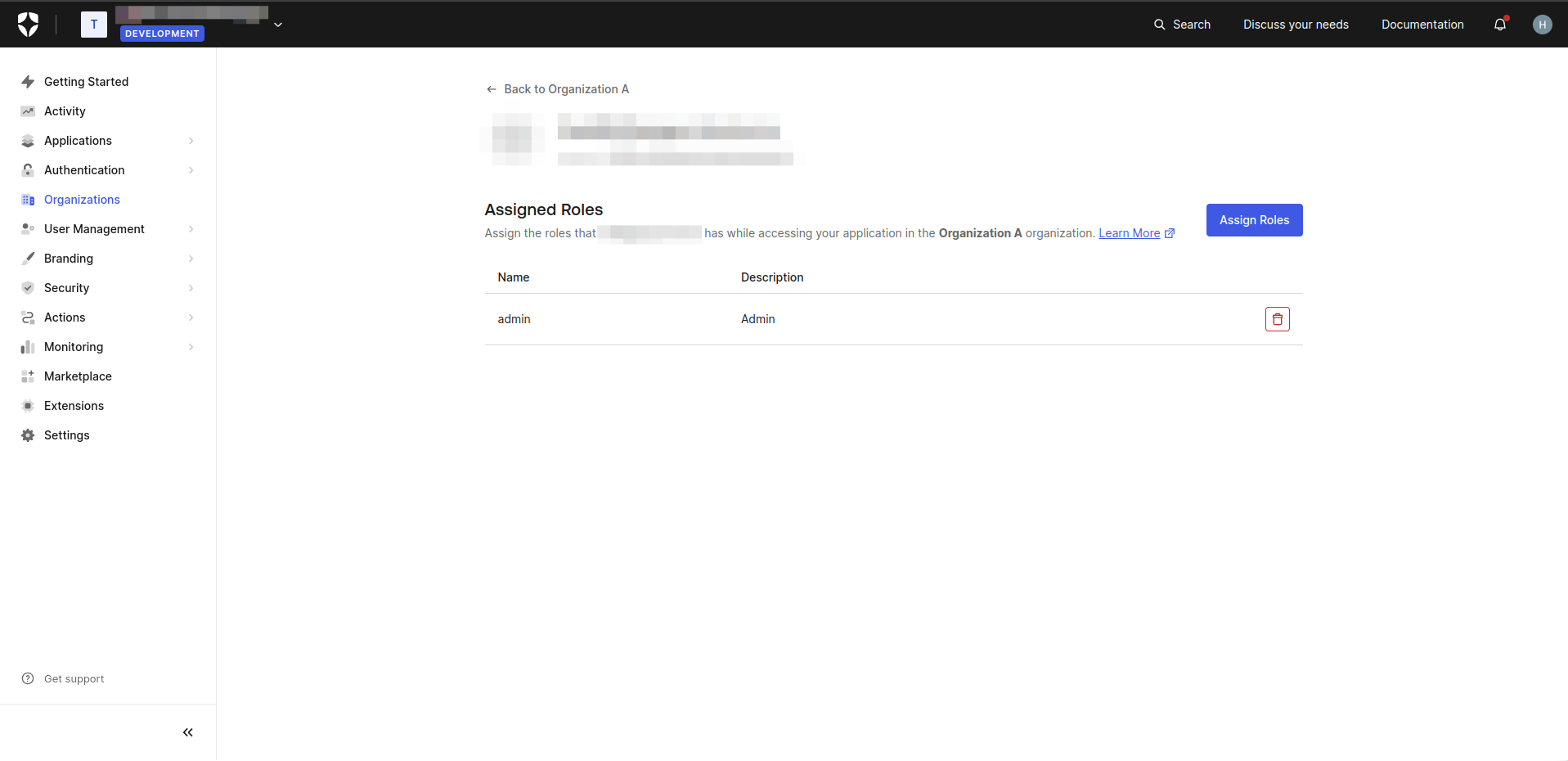
- On the Organization Details screen, navigate to the Connections tab.
- Click the Enable Connections button
- Select Username-Password-Authentication and click Enable Connection
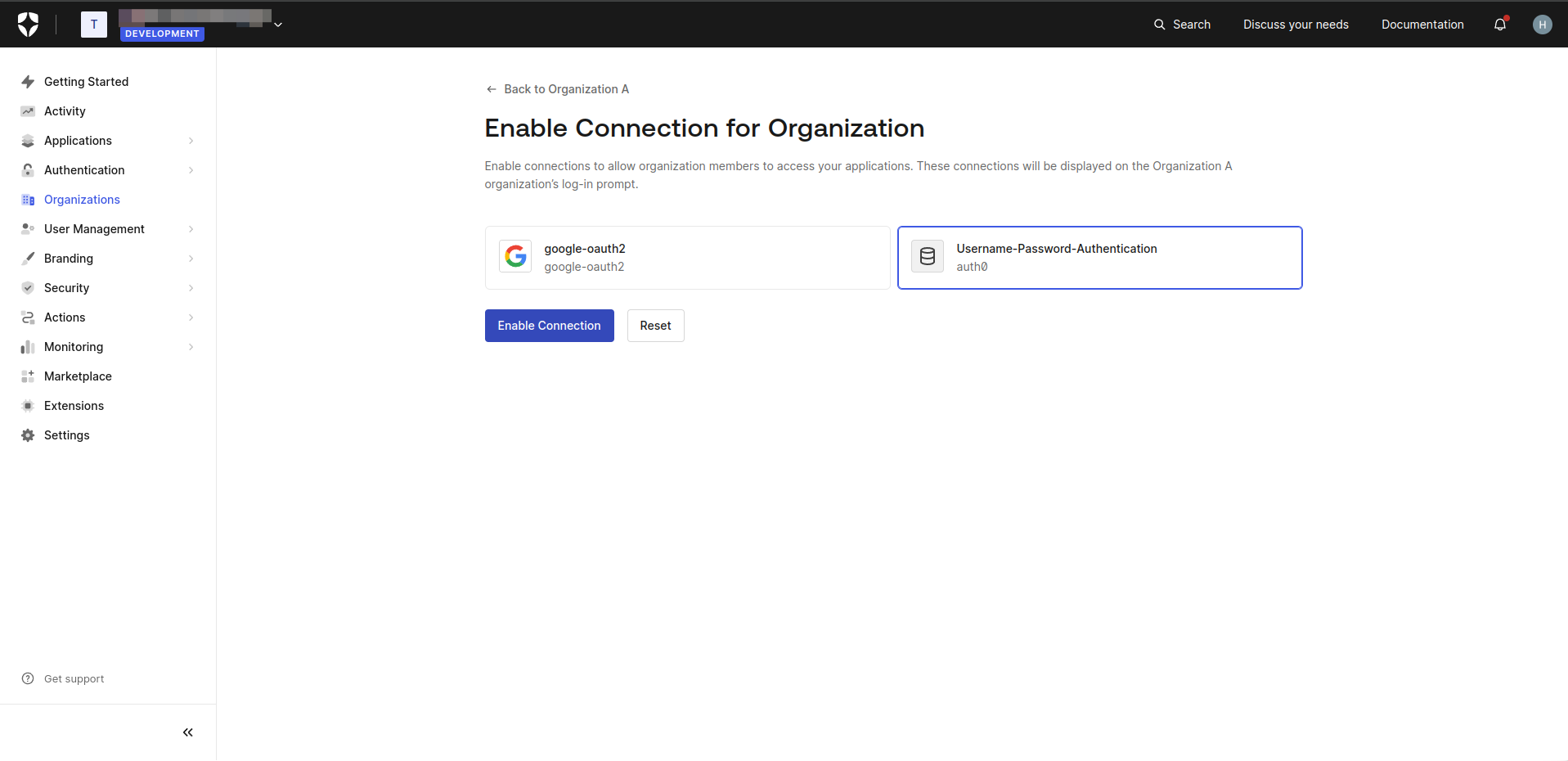
- Select Enable Auto-Membership and Enable Signup on the displayed screen, then click Save.
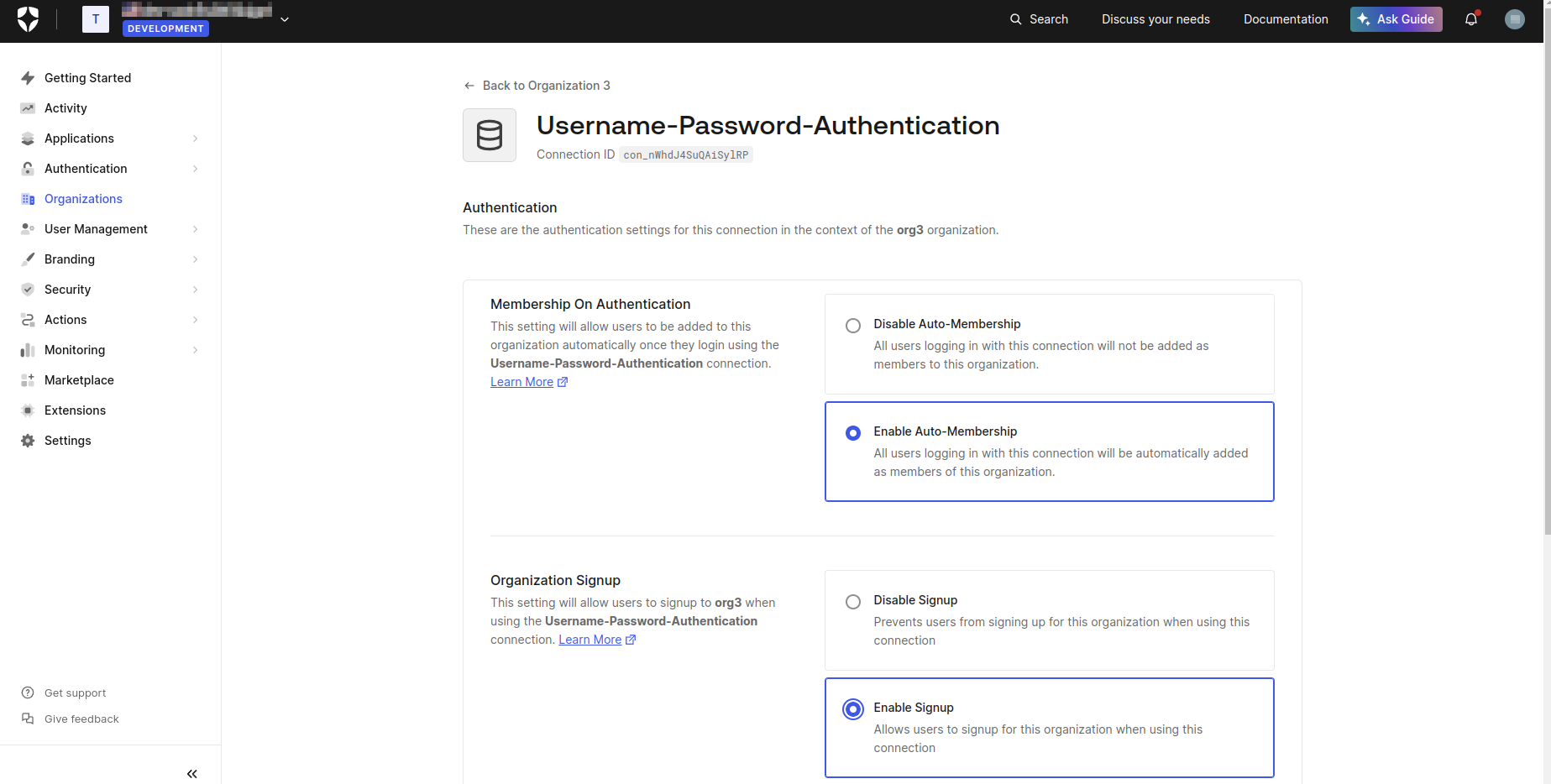
Step 3. Enable Organization for your application
- In the Auth0 dashboard, navigate to the Applications section.
- Select the relevant application.
- On the Application Details screen, navigate to the Organizations tab.
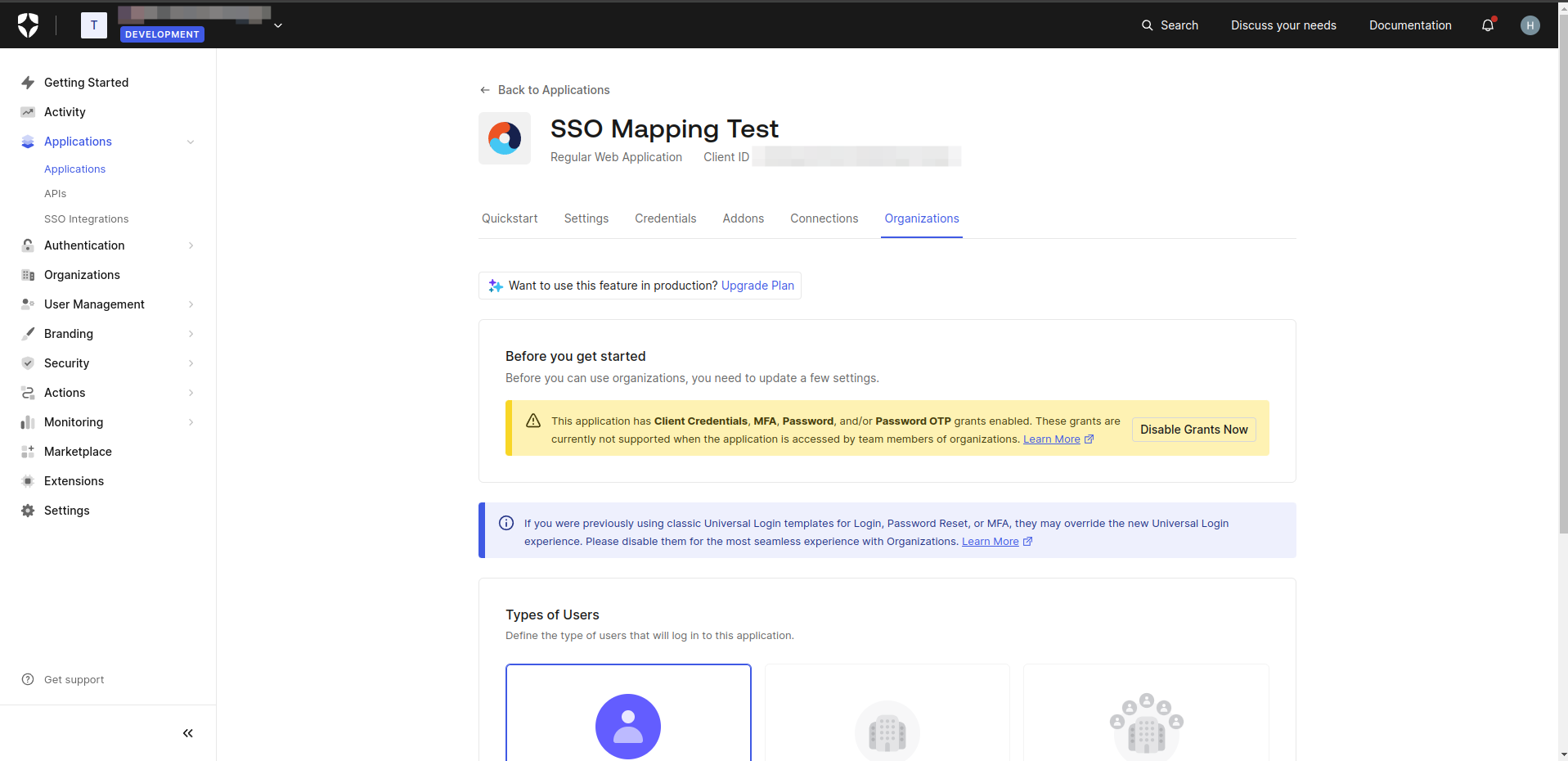
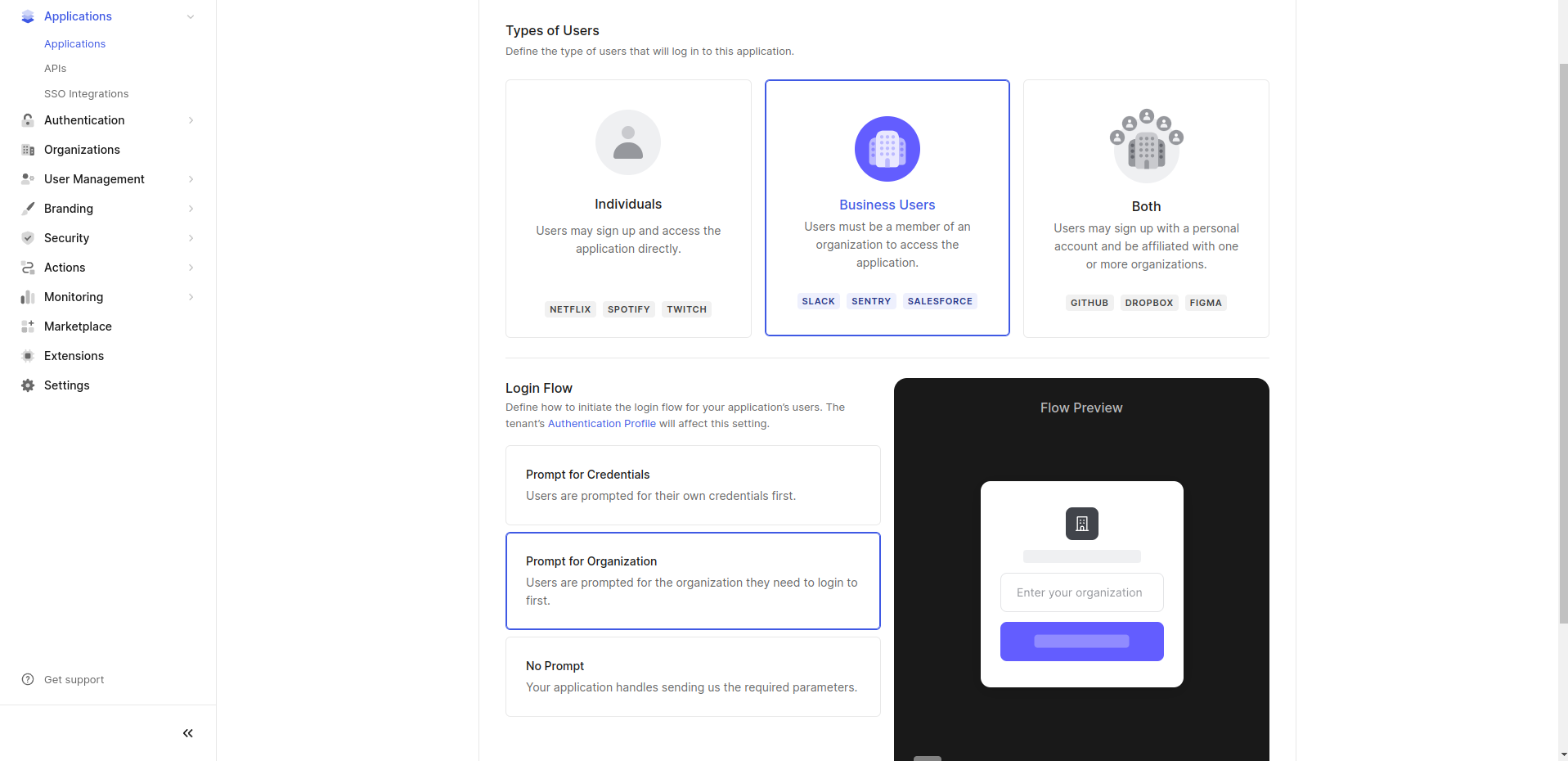
- Click Disable Grants Now.
- Choose Business Users for the type of users and select Prompt for Organization for the login flow.
- Click Save Changes.
Step 4. Define Group And Role Attributes & Claims
The user's group and role values should be included in the token as claims. This enables retrieval of the user's group and role during SSO login. The groups claim is already present in the token. Follow these steps to add the roles claim:
- In the Auth0 dashboard, navigate to the Actions > Library section.
- Click the Create Action button and select Build from Scratch.
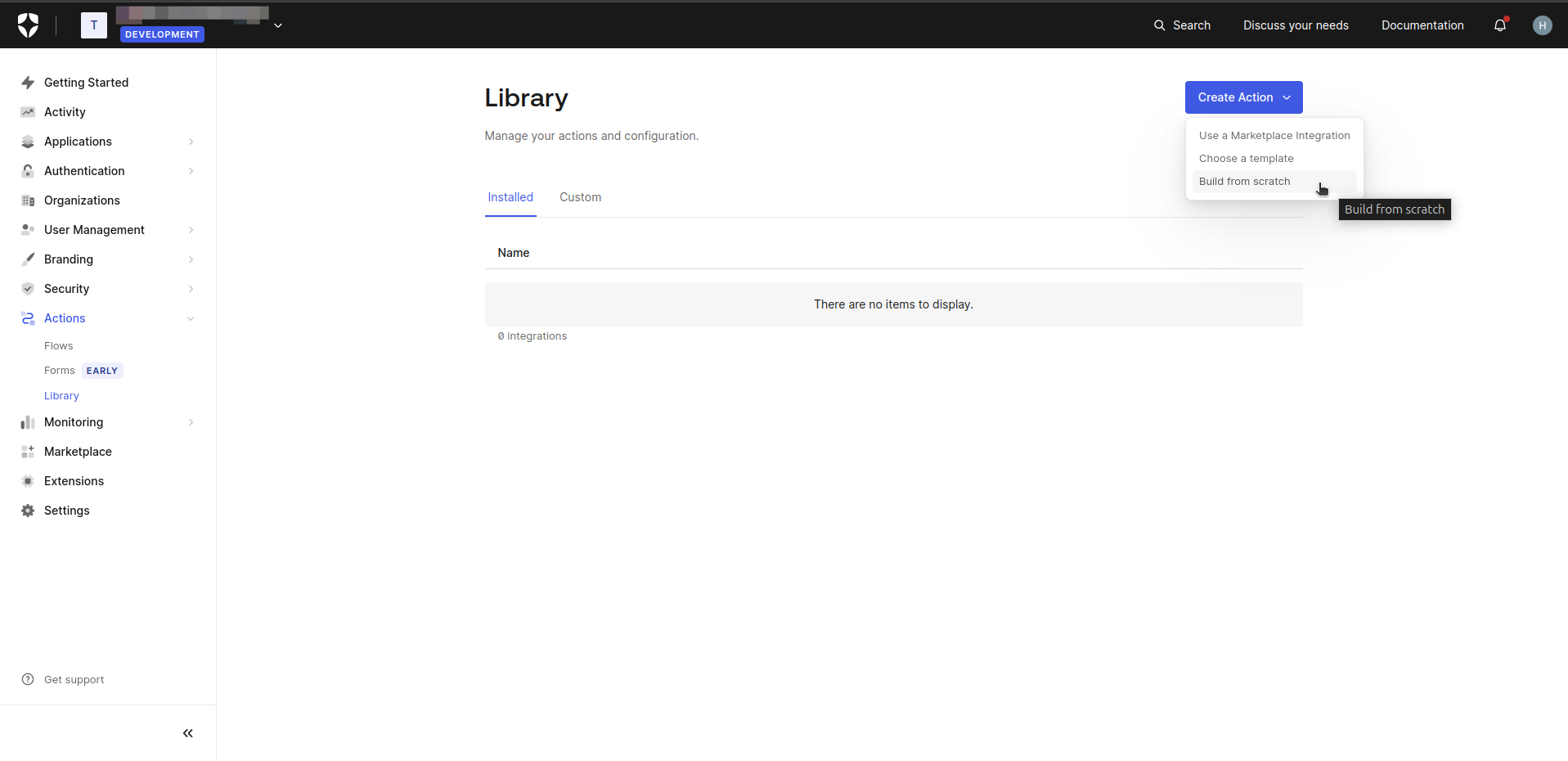
- Enter an appropriate name for the Custom Action in the popup window. Keep the remaining settings at their default values,as shown in the image below.
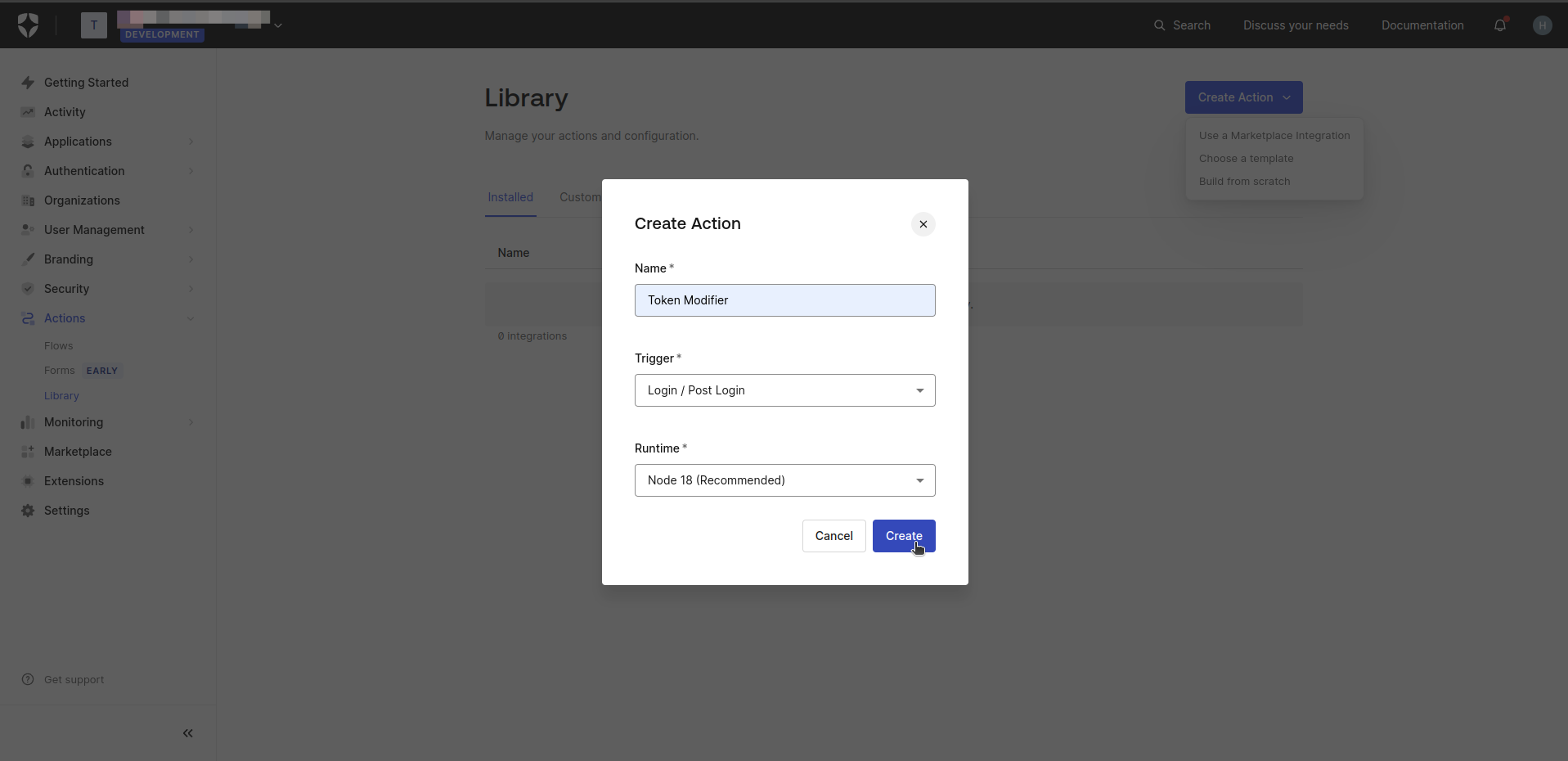
- On the Custom Action Details screen, copy and paste following Javascript code to code editor.
exports.onExecutePostLogin = async (event, api) => {
const namespace = 'your_namespace_';
if (event.authorization) {
api.idToken.setCustomClaim(`${namespace}roles`, event.authorization.roles);
api.accessToken.setCustomClaim(`${namespace}roles`, event.authorization.roles);
}
}
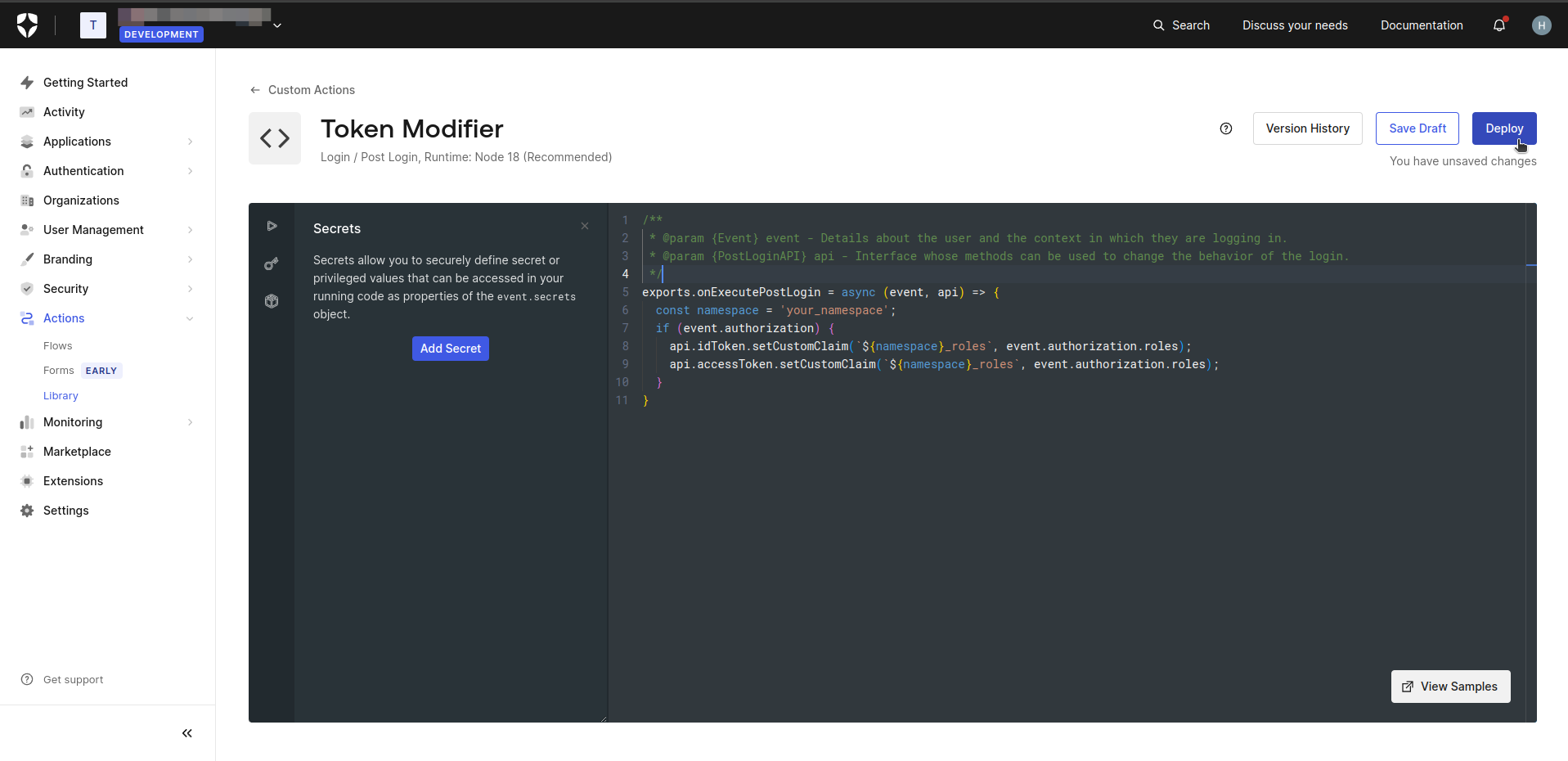
- Finally click on the Deploy button.
- In the Auth0 dashboard, navigate to the Flows section.
- Click the Login.
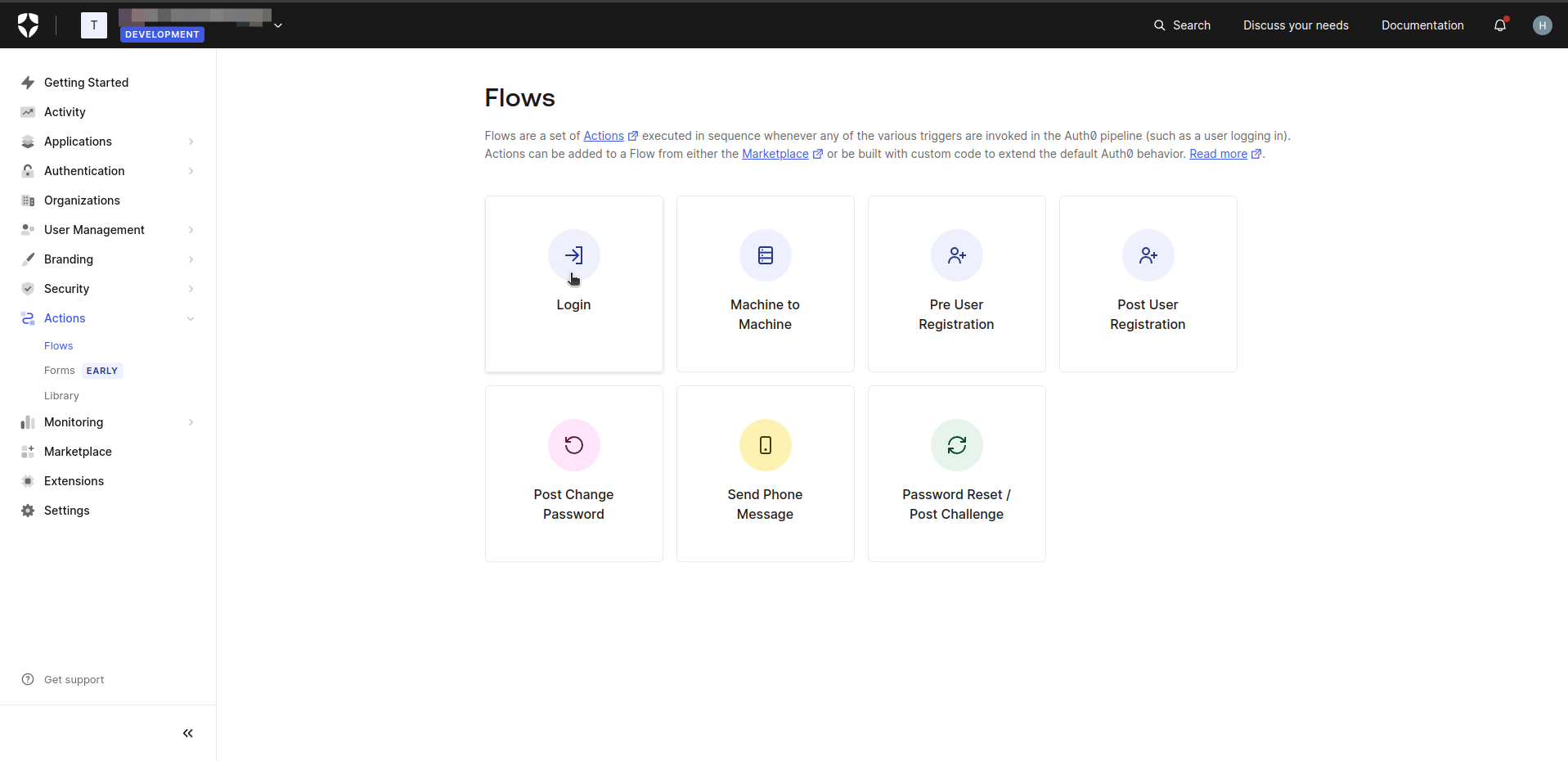
- Drag and drop the custom action created previously. The role claim has been added to the token.
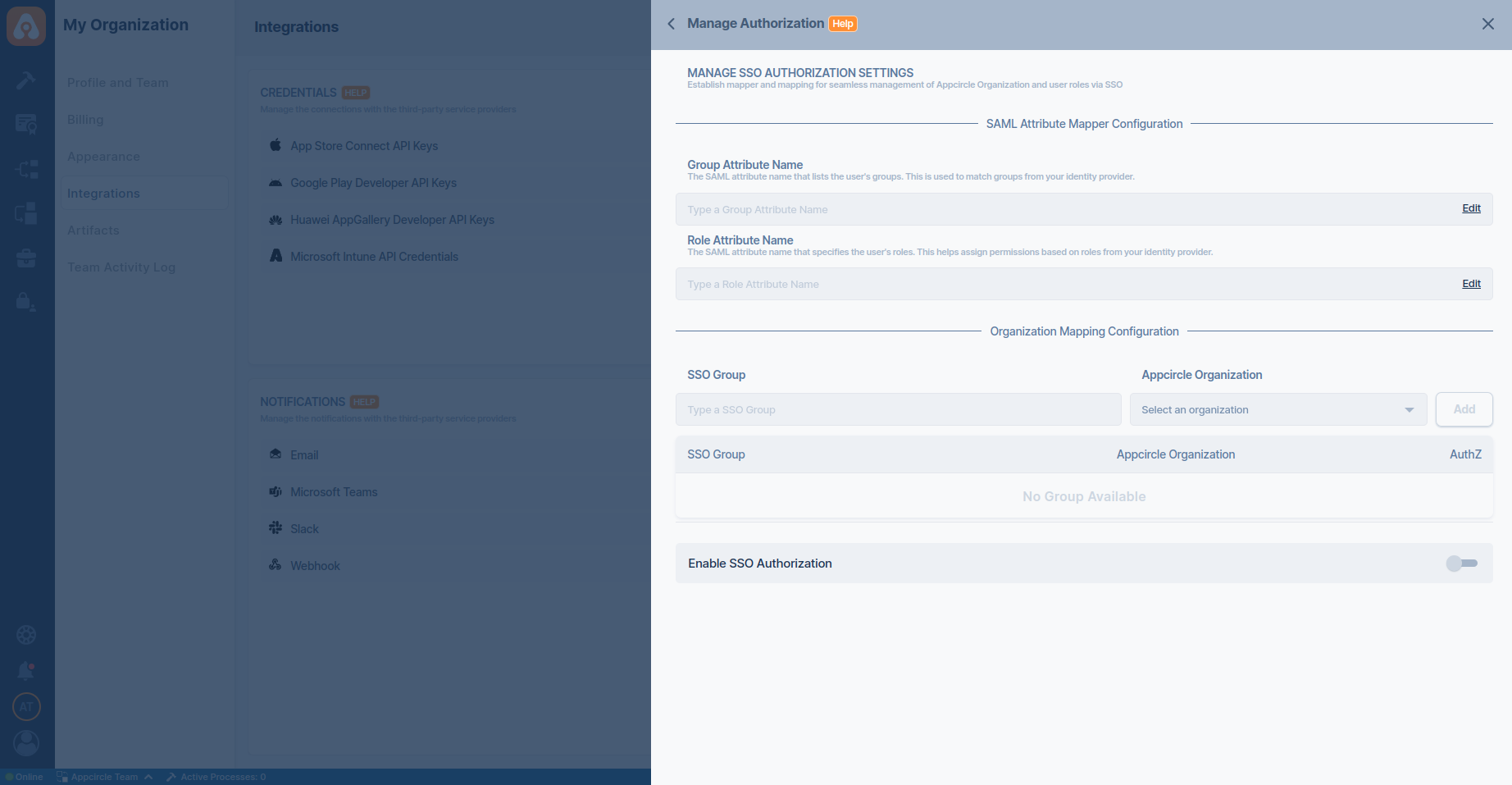
Step 5. Define Group and Role Claim Names in Appcircle
- Navigate to the Set up OpenID Provider screen in Appcircle, which you accessed during the SSO setup in the "General Configuration Steps."
- Enter the Group Claim Name as org_id and the Role Claim Name as your_namespace_roles. Note that the role claim is created as a custom claim in Auth0, so use the name you determined earlier.
Auth0 (SAML)
Step 1. Create Roles
- In the Auth0 dashboard, navigate to the User Management > Roles section.
- Click Create Role button. Create necessary roles.

Step 2. Create Organization
- In the Auth0 dashboard, navigate to the Organization section.
- Click Create Organization button to create organizations.

- Click the created organization to navigate to Organization Details.
- On the Organization Details screen, click the Members tab to manage members of organization.
- Click the Add Members button to add users who will become members of your organization.

- On the Members screen, click the three dots and select Assign Roles. Assign the desired roles to users for organization.

- On the Organization Details screen, navigate to the Connections tab.
- Click the Enable Connections button
- Select Username-Password-Authentication and click Enable Connection

- Select Enable Auto-Membership and Enable Signup on the displayed screen, then click Save.

Step 3. Enable Organization for your application
- In the Auth0 dashboard, navigate to the Applications section.
- Select the relevant application.
- On the Application Details screen, navigate to the Organizations tab.

- Click Disable Grants Now.
- Choose Business Users for the type of users and select Prompt for Organization for the login flow.
- Click Save Changes.

Step 4. Define Group And Role Attributes & Claims
The user's group and role values should be included in the token as claims. This enables retrieval of the user's group and role during SSO login. The groups claim is already present in the token. Follow these steps to add the roles claim:
- In the Auth0 dashboard, navigate to the Actions > Library section.
- Click the Create Action button and select Build from Scratch.

- Enter an appropriate name for the Custom Action in the popup window. Keep the remaining settings at their default values,as shown in the image below.

- On the Custom Action Details screen, copy and paste following Javascript code to code editor.
exports.onExecutePostLogin = async (event, api) => {
const namespace = 'your_namespace_';
if (event.authorization) {
api.idToken.setCustomClaim(`${namespace}roles`, event.authorization.roles);
api.accessToken.setCustomClaim(`${namespace}roles`, event.authorization.roles);
}
}

- Finally click on the Deploy button.
- In the Auth0 dashboard, navigate to the Flows section.
- Click the Login.

- Drag and drop the custom action created previously. The role claim has been added to the token.
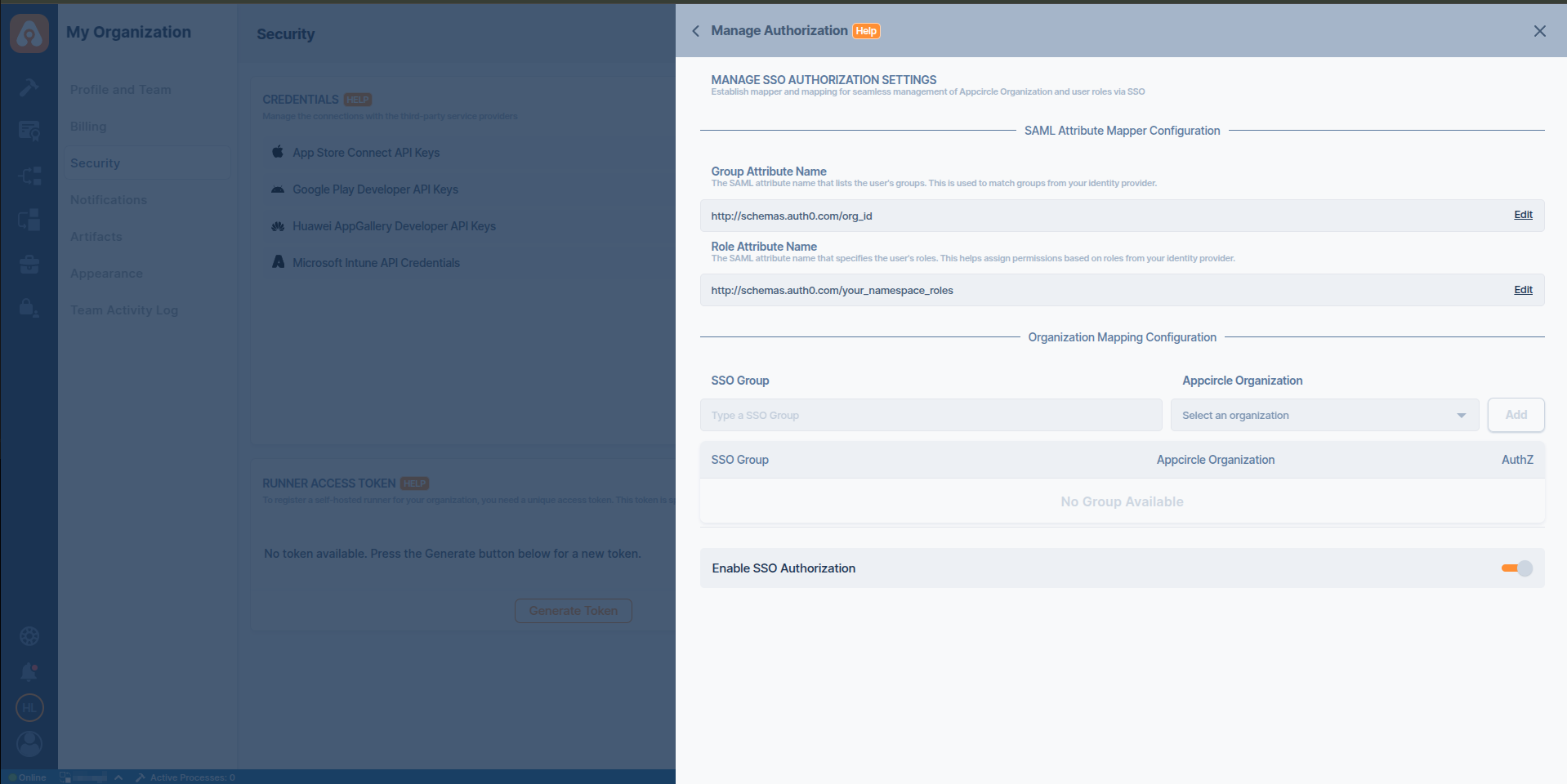
Step 5. Define Group and Role Attributes names in Appcircle
- Navigate to the Set up OpenID Provider screen in Appcircle, which you accessed during the SSO setup in the "General Configuration Steps."
- Enter the Group Attribute Name as
http://schemas.auth0.com/org_idand the Role Attribute Name ashttp://schemas.auth0.com/your_namespace_roles. Note that the role attribute is created as a custom attribute in Auth0, so you must use the name you determined previously.
Microsoft Entra ID (formerly Azure Active Directory)
Microsoft Entra ID (SAML)
Step 1. Create Groups in Microsoft Entra ID
- Log in to Azure as an admin and navigate to Azure Services > Microsoft Entra ID
- Navigate to the Manage > Groups section from left menu.
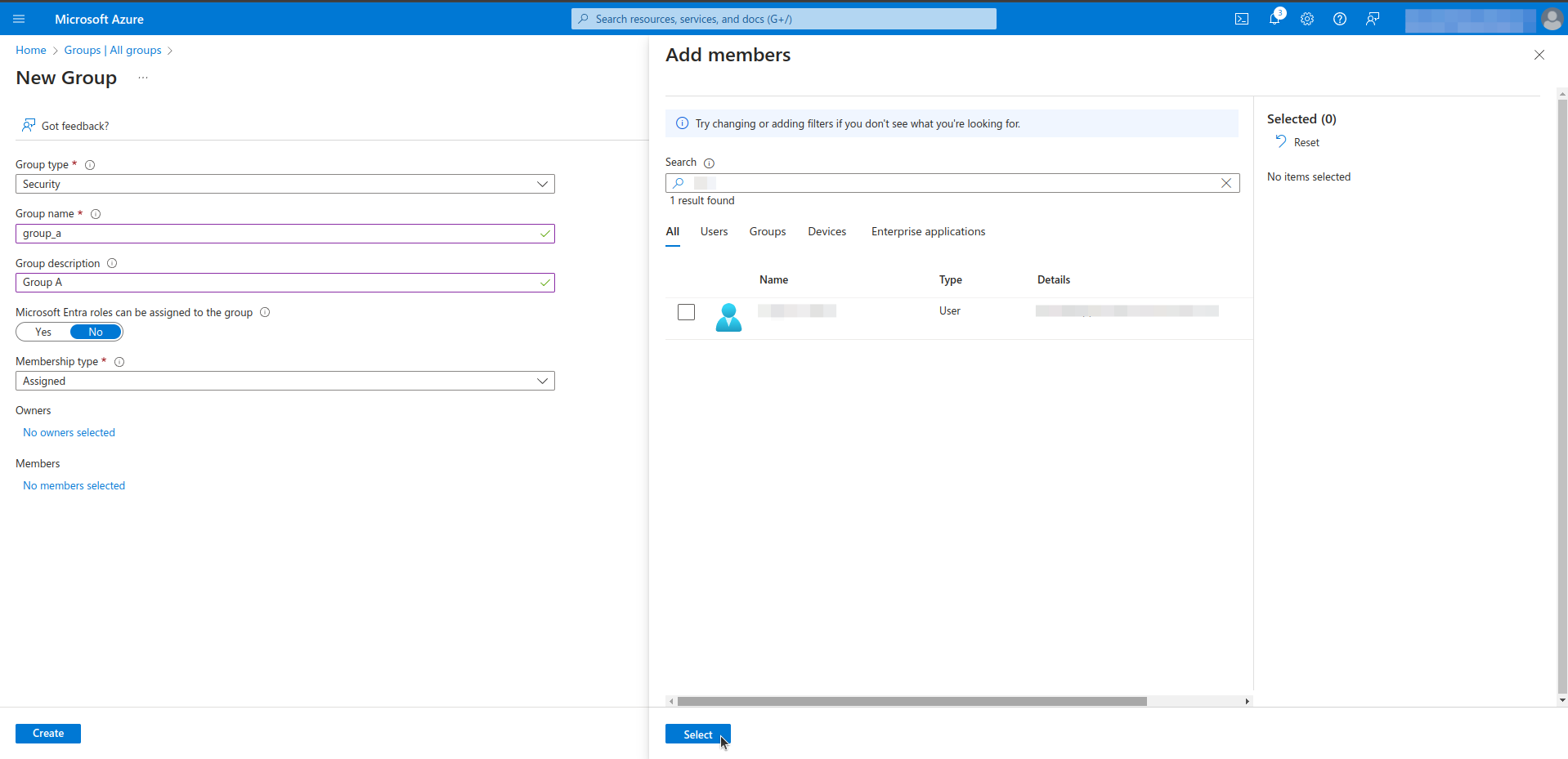
- Click the New Group.
- Assign a proper name and description to the new group. Designate an owner and members to the group.
Step 2. Create Roles in Microsoft Entra ID
- Navigate to the Manage > App registrations section from left menu.
- Select All applications to view a list of all your applications and locate your application.
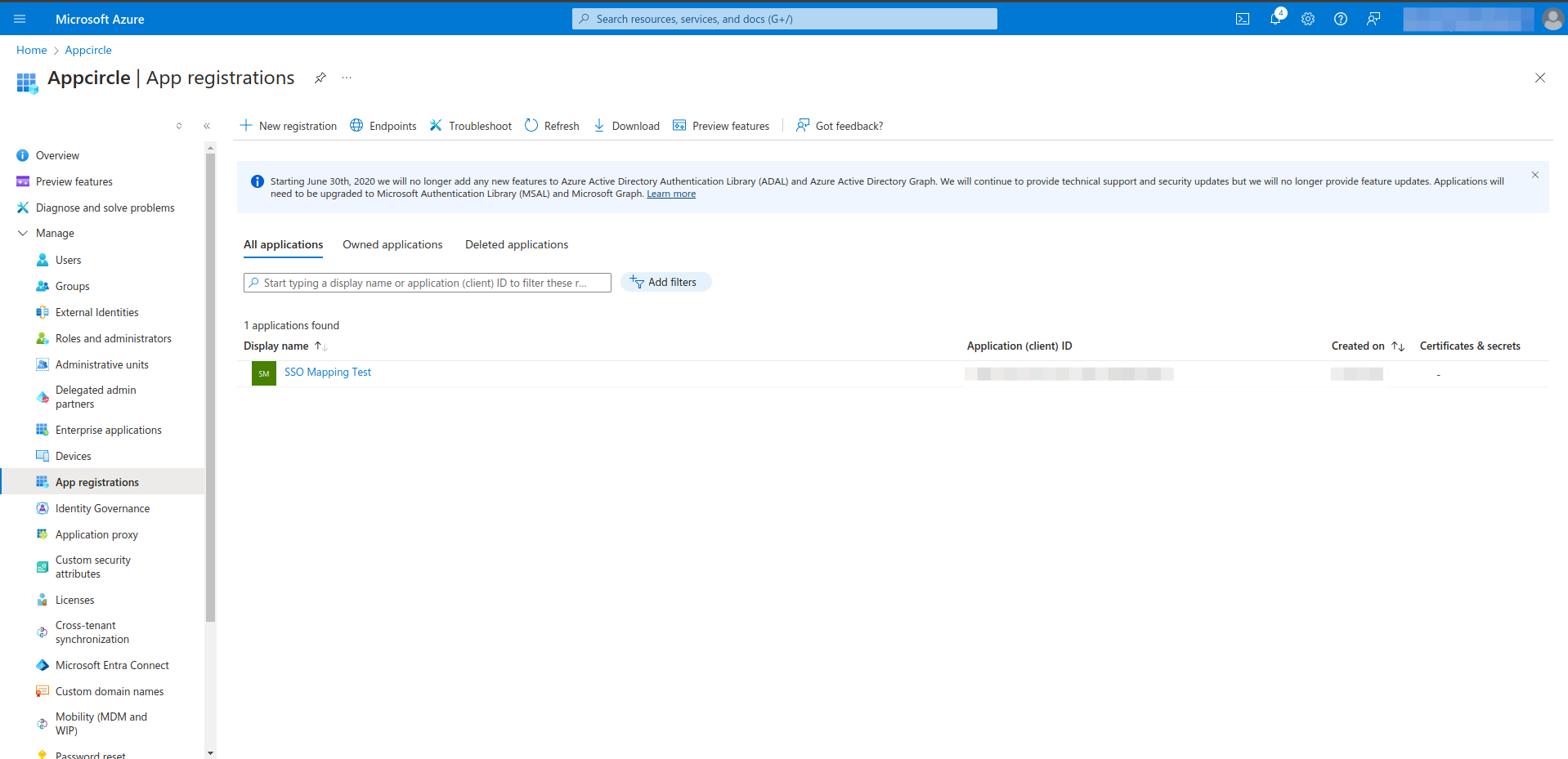
- Navigate to the Manage > App Roles section from left menu.
- Click the Create app role. Create a new app role as shown in the image below.
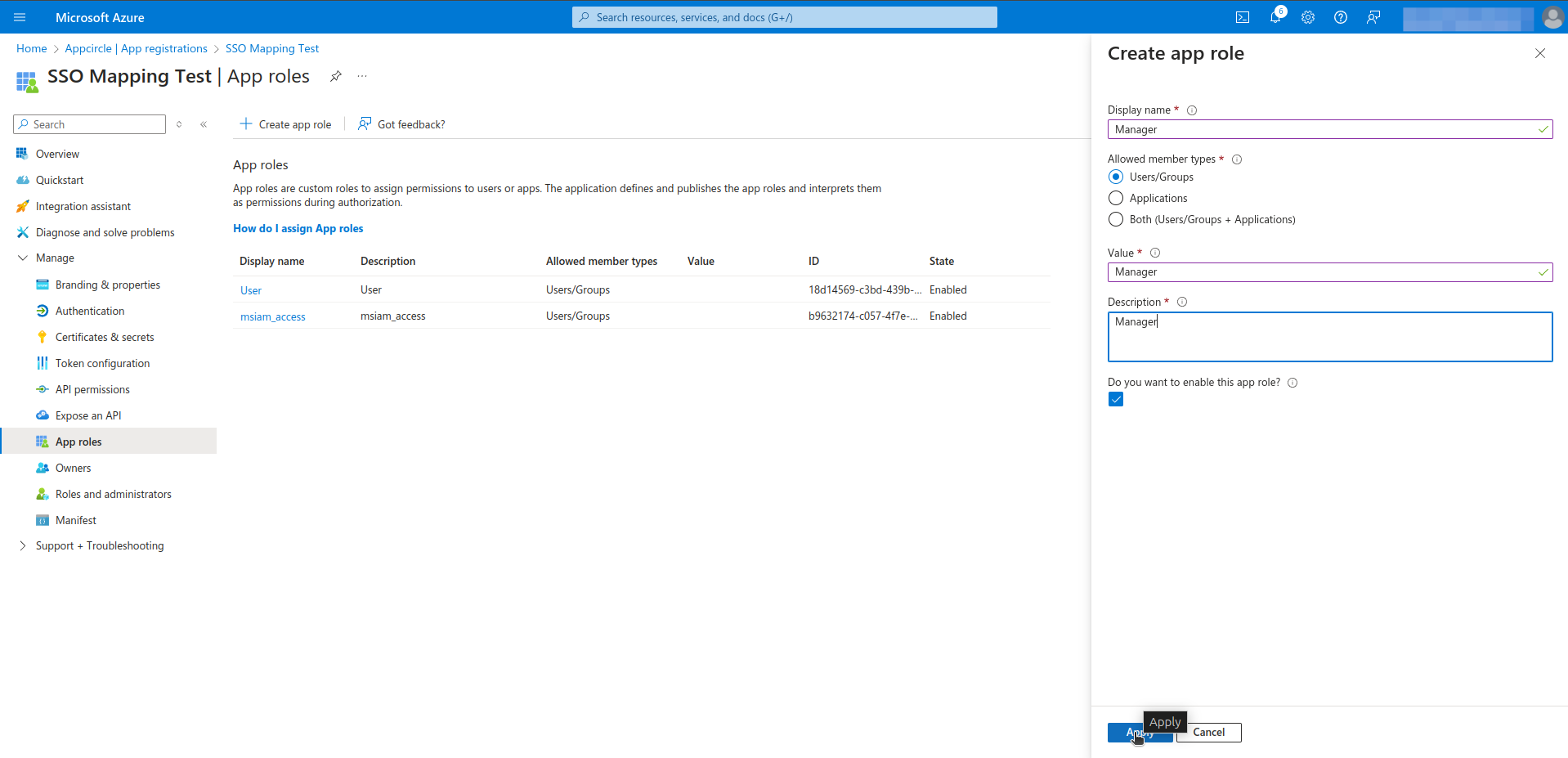
- Navigate to the Manage > API permissions section from left menu.
- Click the Add Permissions.
- Select the My APIs and click on your application name.
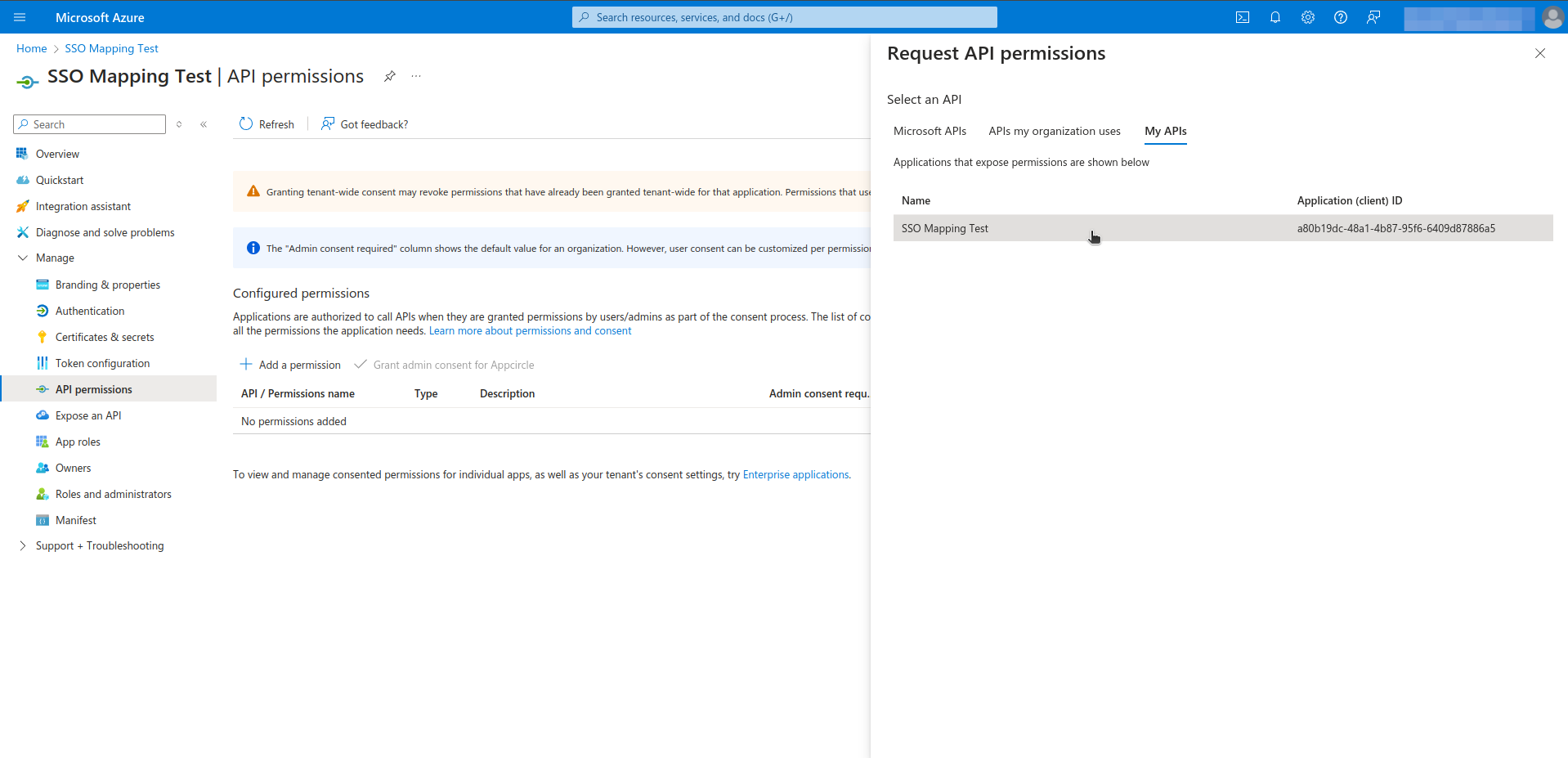
- Select permissions and click on Add permissions.
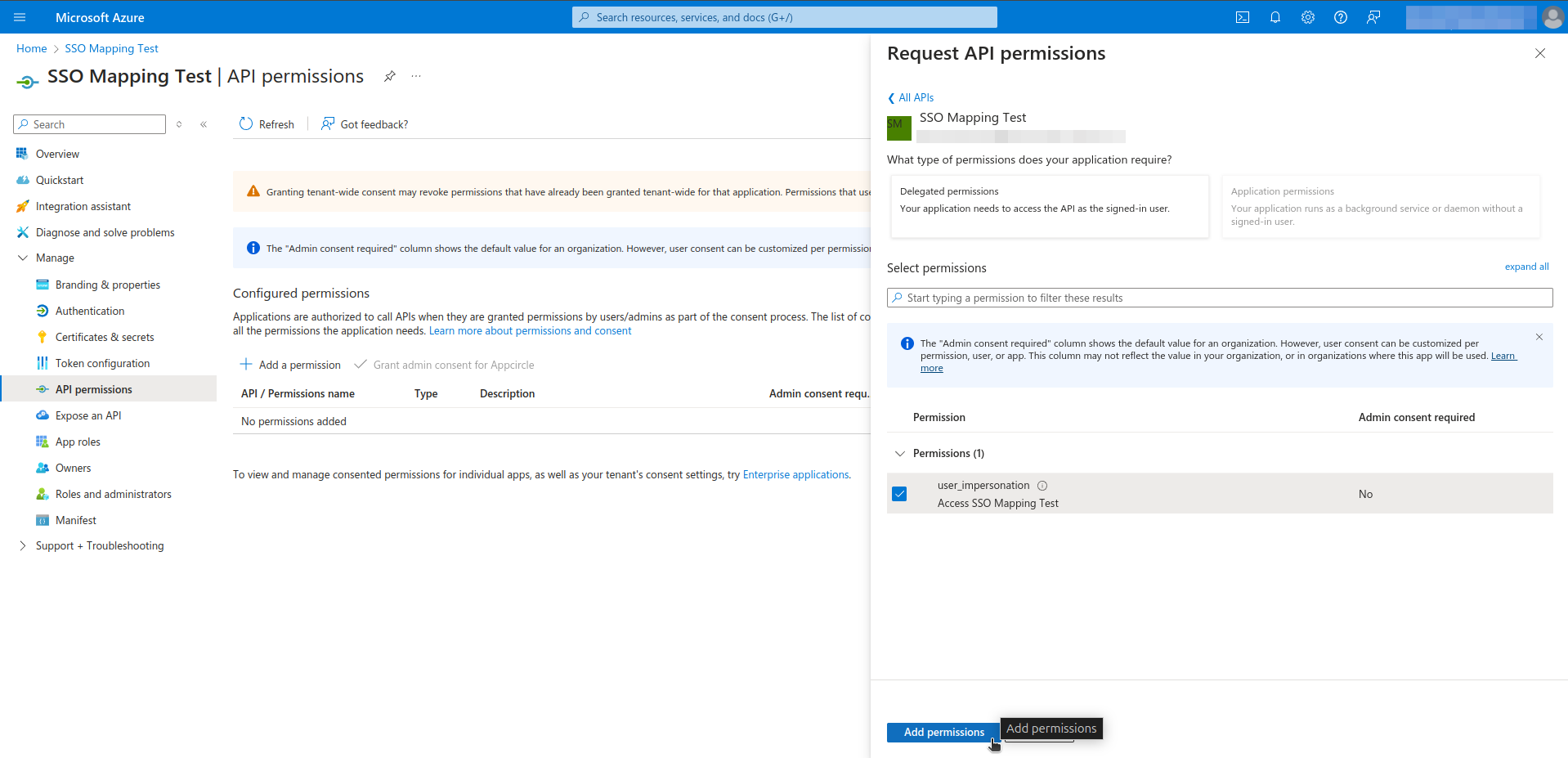
Step 3. Assign user, group and roles to application in Microsoft Entra ID
- Navigate to the Azure Services > Microsoft Entra ID.
- Navigate to the Manage > Enterprise applications section from left menu.
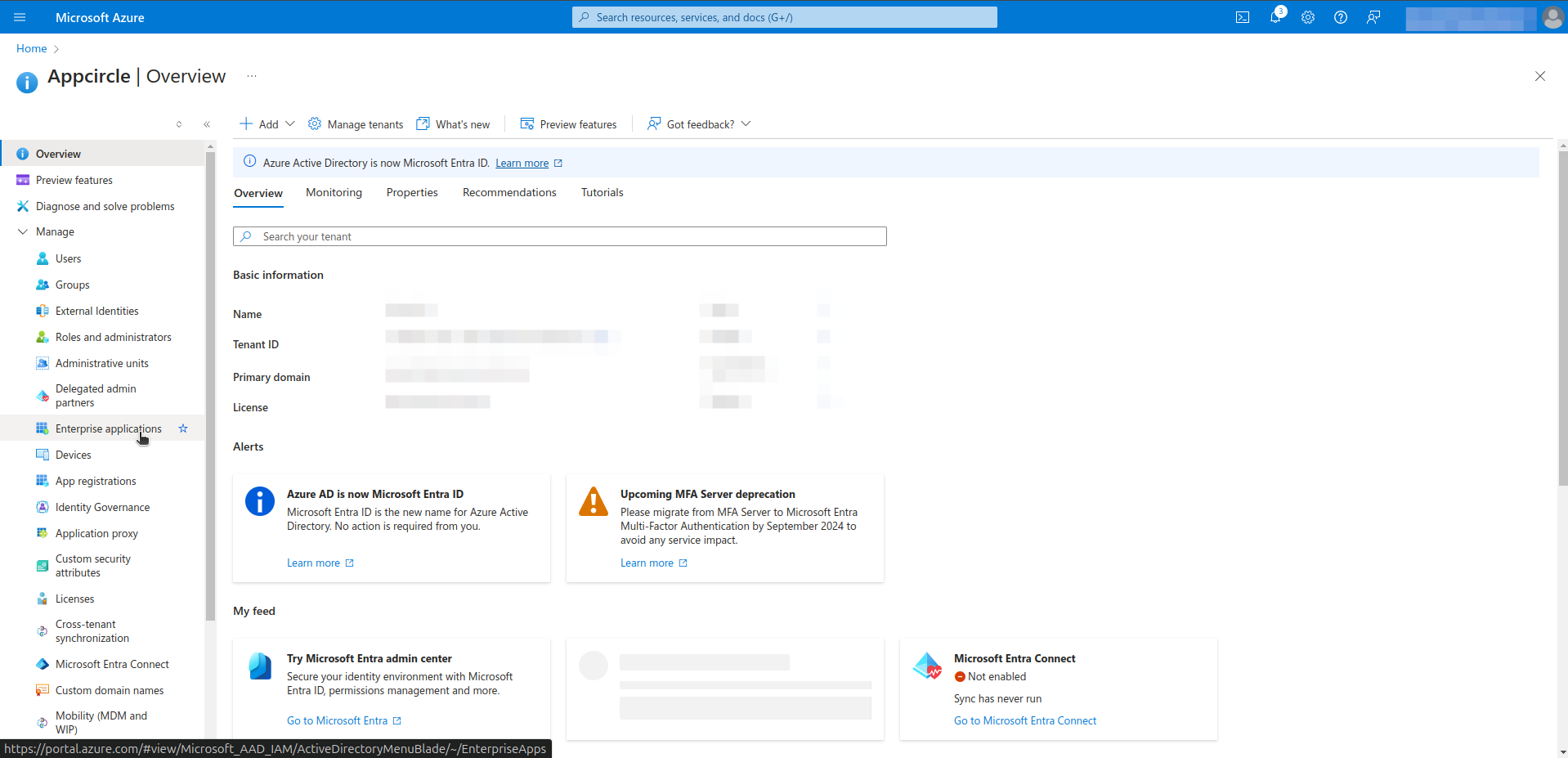
- Click your application.
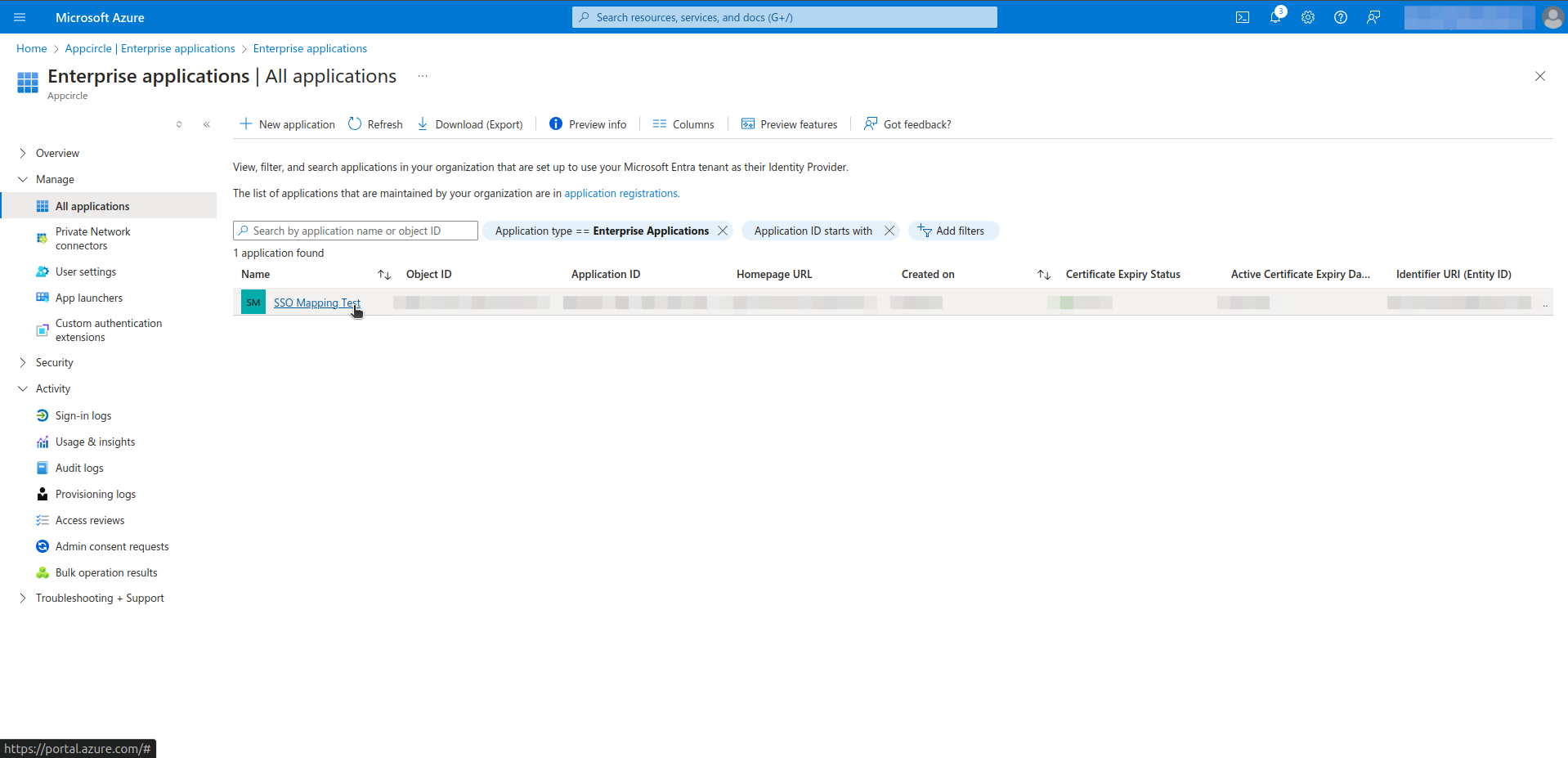
- Click Assign users and groups.
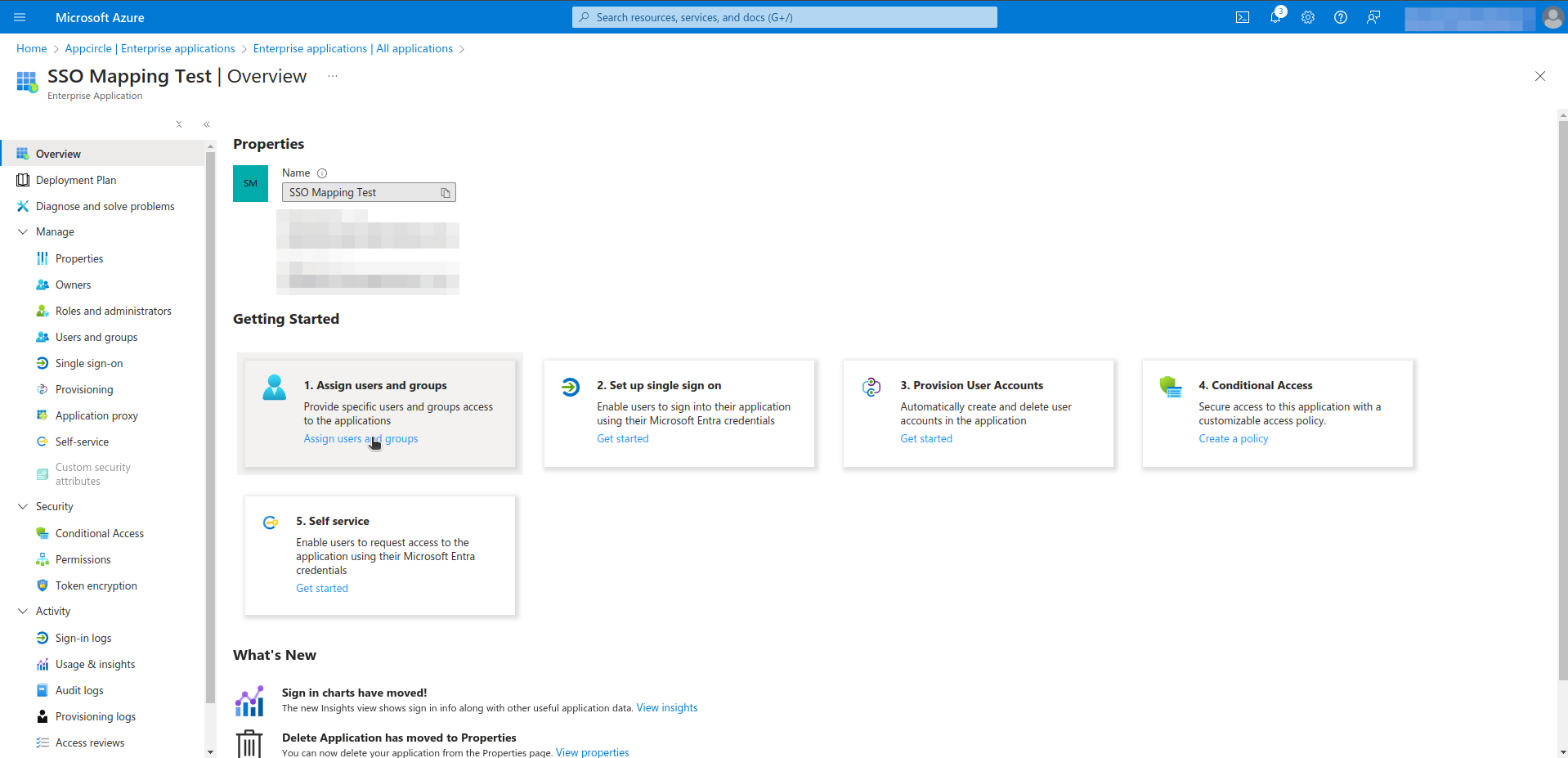
- Click Add user/group.
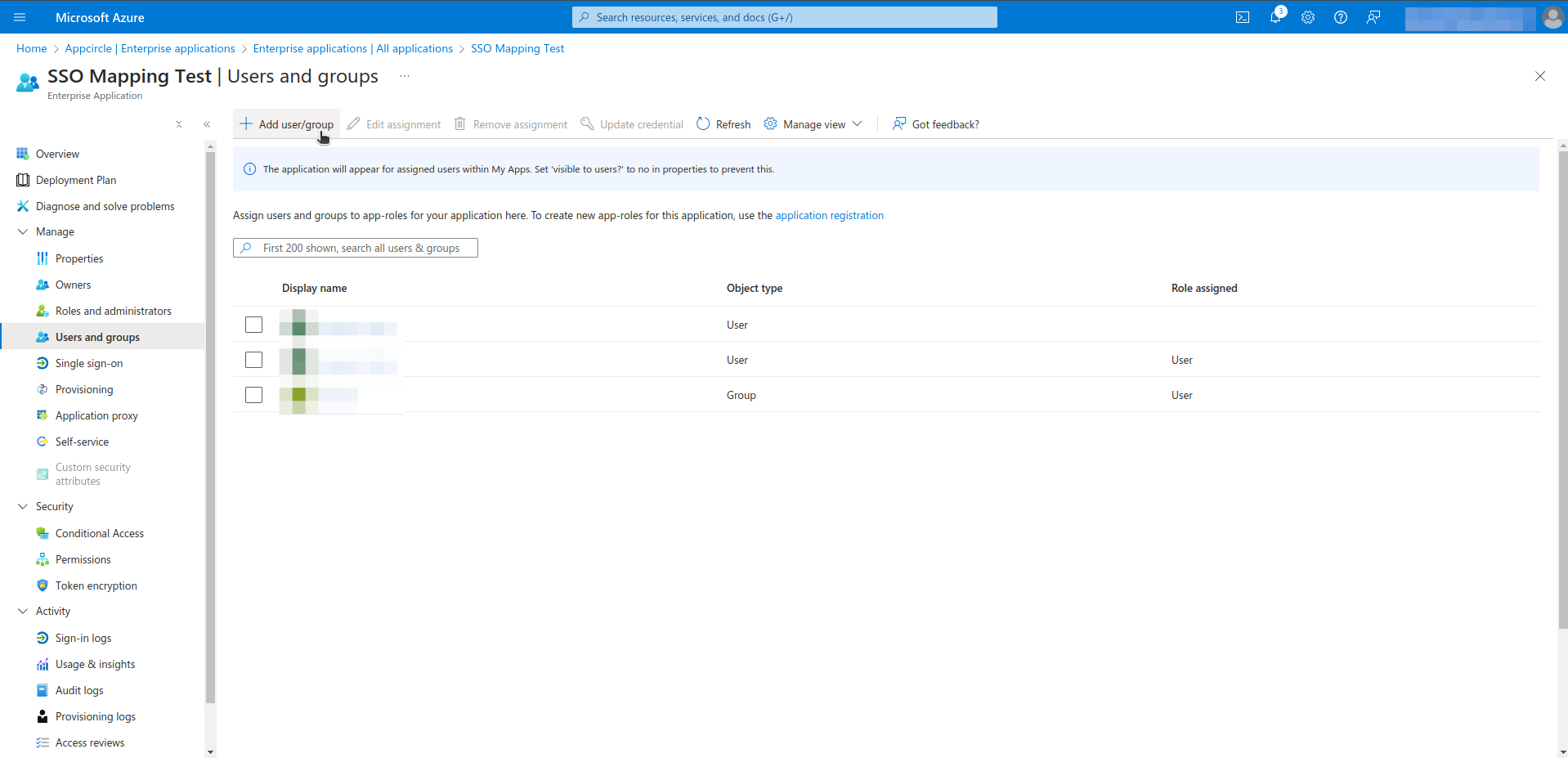
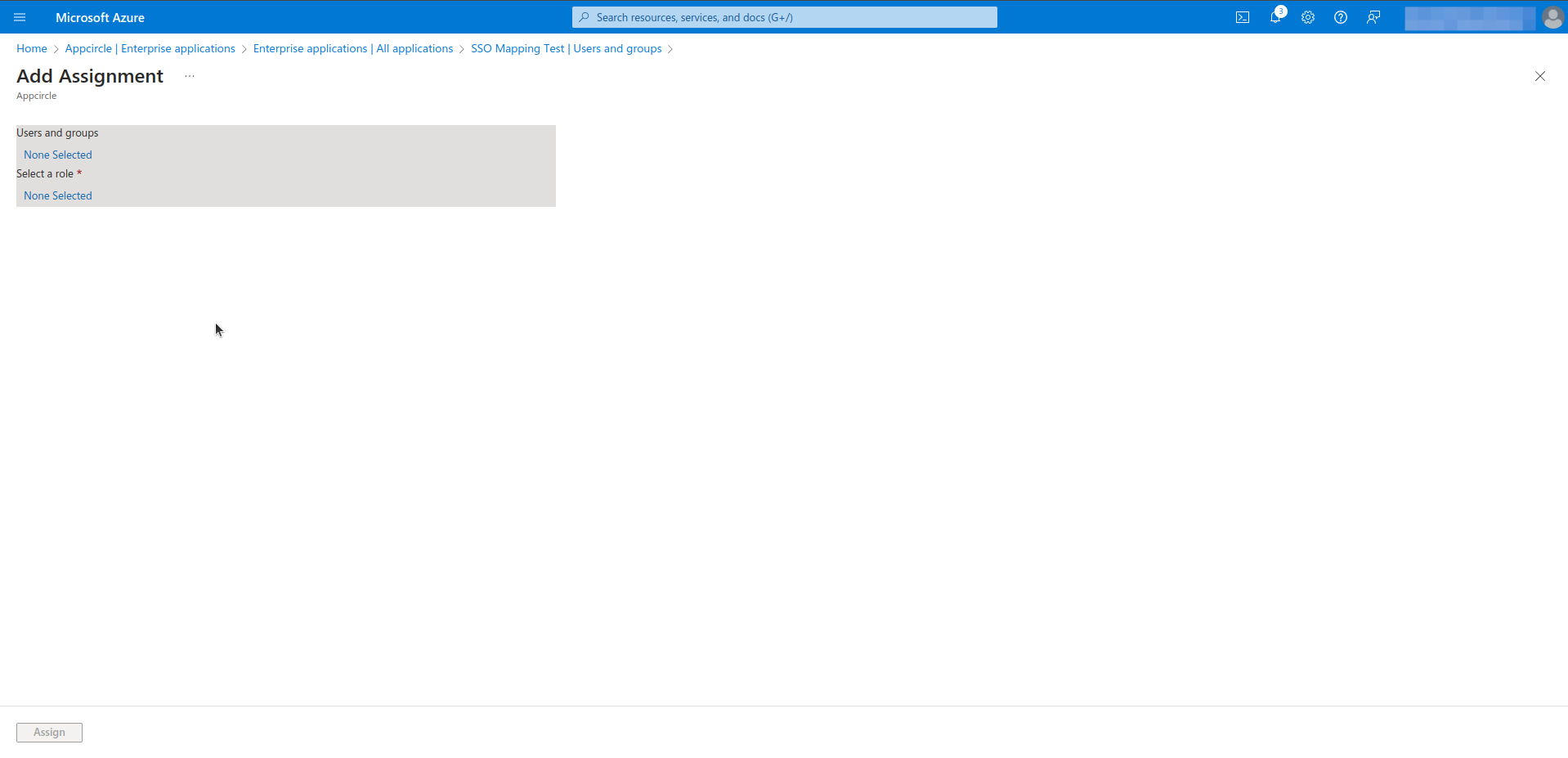
- Select users, groups and role. This process can be repeated as needed.
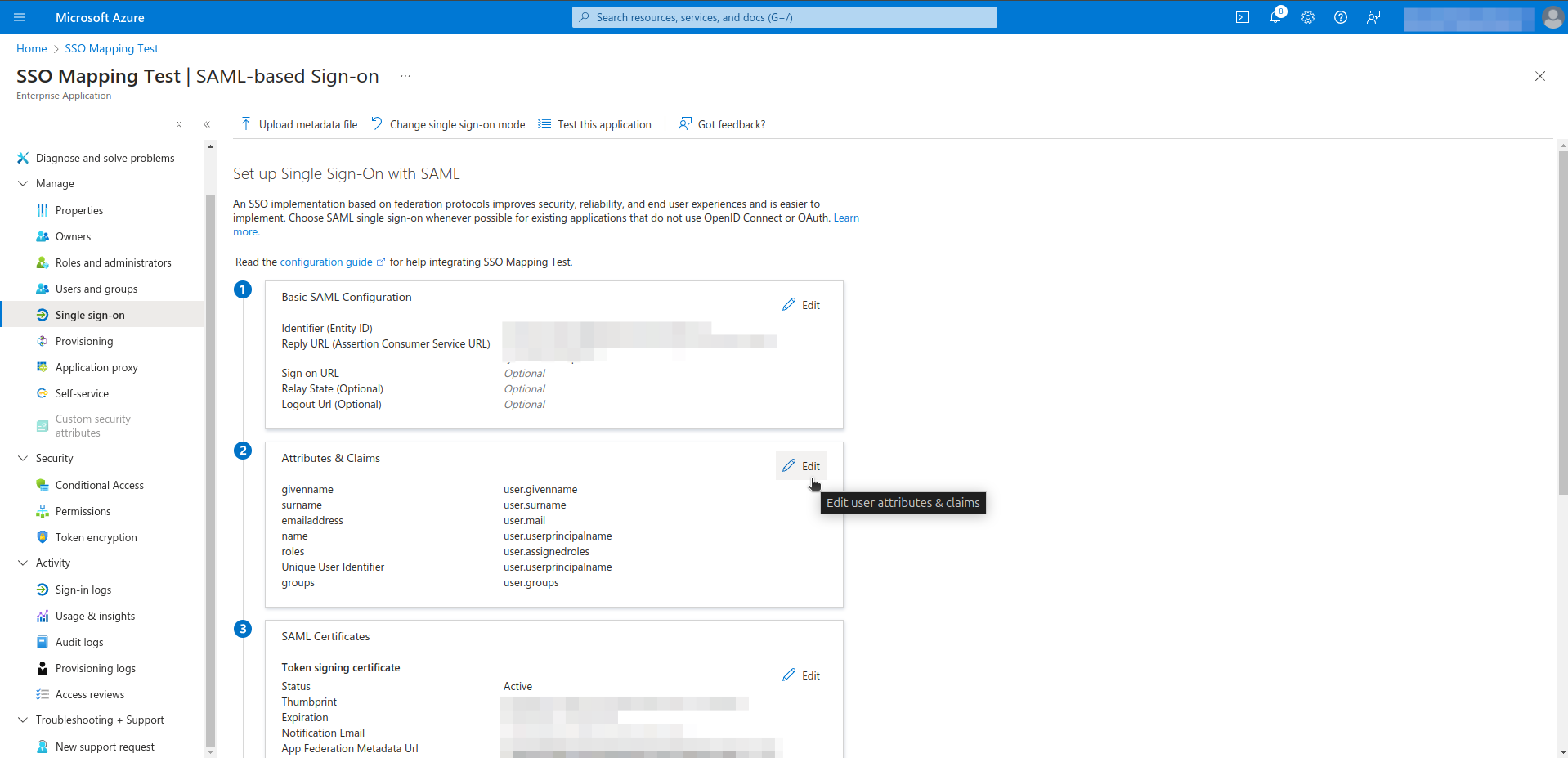
Step 4. Define Group and Role Attributes & Claims in Microsoft Entra ID
- Navigate to the Manage > Single sign-on section from left menu.
- Click Edit in Attributes & Claims section.
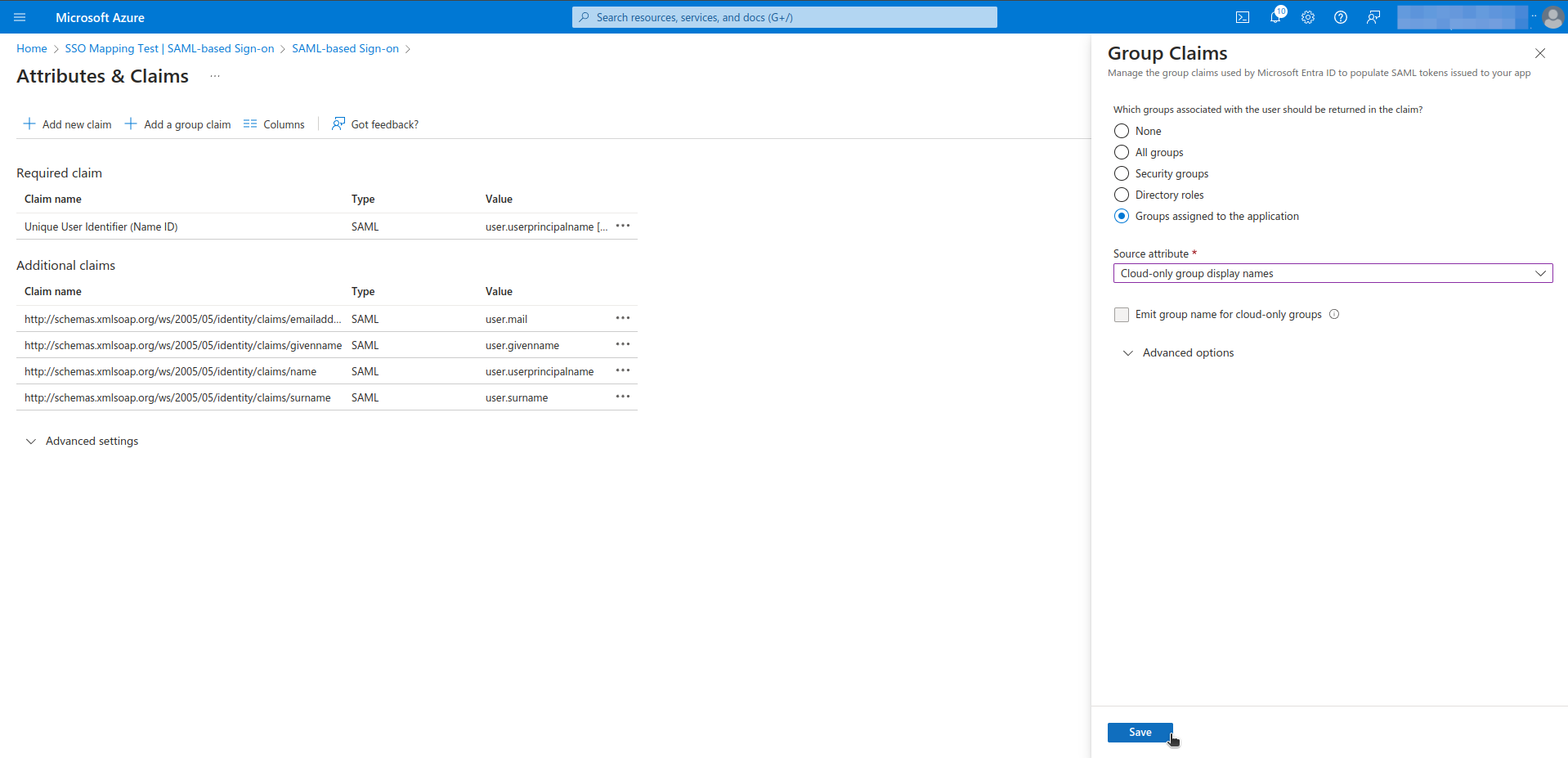
- Click the Add a Group Claim.
- Select the Groups assigned to the application
- Select the Cloud only group display names as source attribute.
- Then click on the Save button
- Click Add new claim.
- Enter name as roles
- Select user.assignedroles as source attribute.
- Then click on Save.
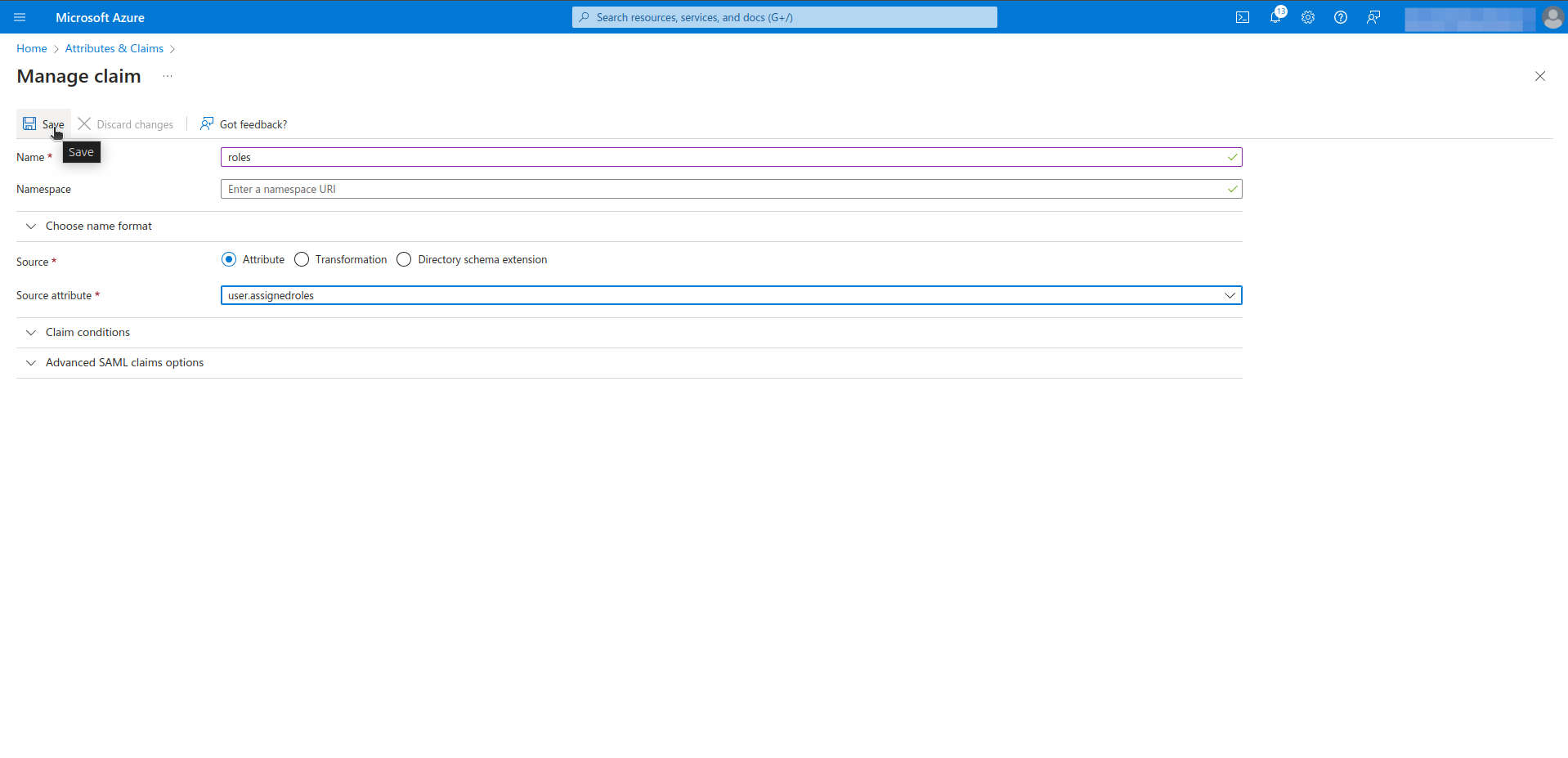
Step 5. Define Group and Role Attribute names in Appcircle
- Navigate to the Set up SAML SSO Provider screen in Appcircle, which you accessed during the SSO setup in the "General Configuration Steps."
- Enter Group Attribute Name as
http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsand Role Attribute Name asroles.
Okta
Okta (OpenID Connect)
Step 1. Create Groups and Define Group Claim
- Navigate to the Directory > Groups section in the Okta Dashboard
- Create the groups as needed.
- Assign users to groups.
- Navigate to the Applications > Applications section from left navigation menu.
- Select your application from the list
- Navigate to the Sign on tab.
- Click Edit for OpenID Connect ID Token.
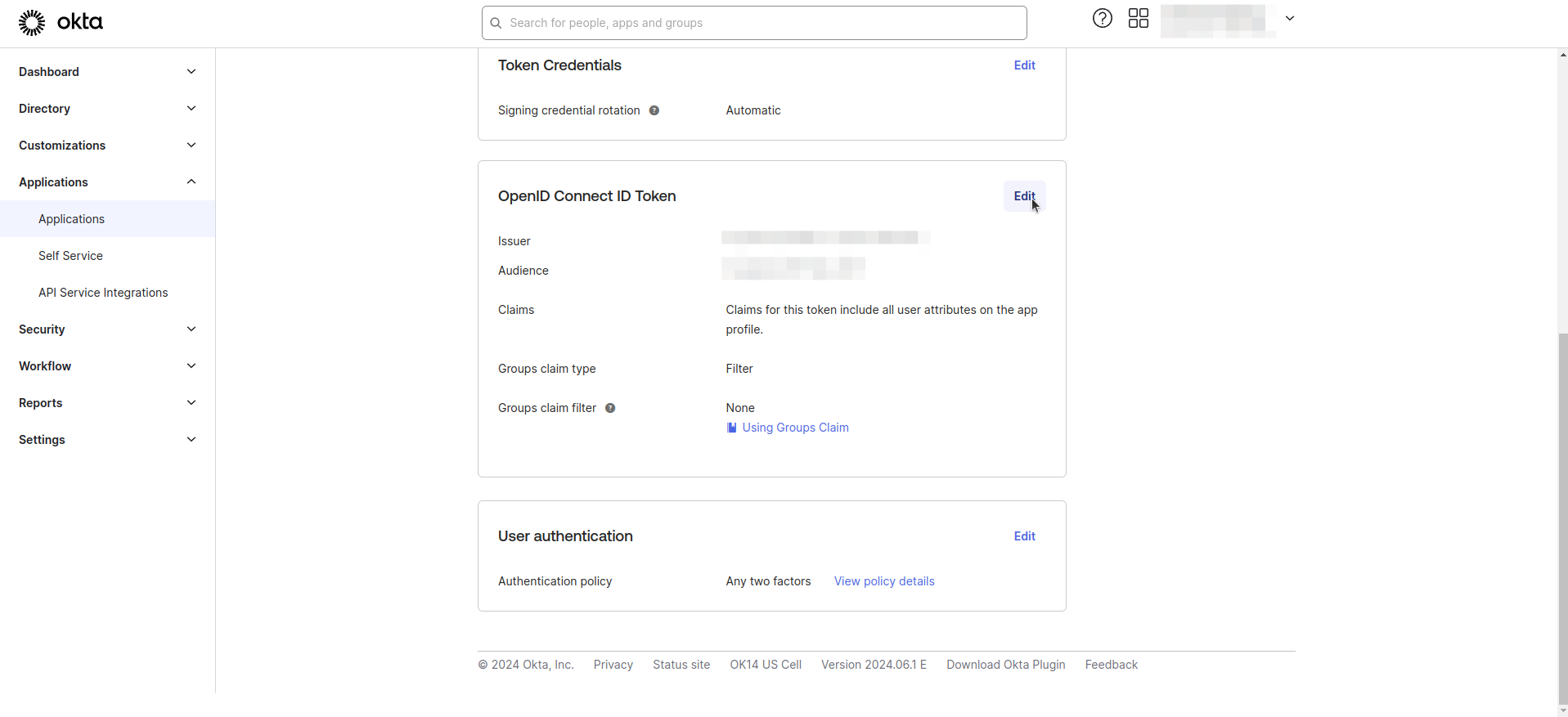
- Enter Groups claim filter as shown in the image below.
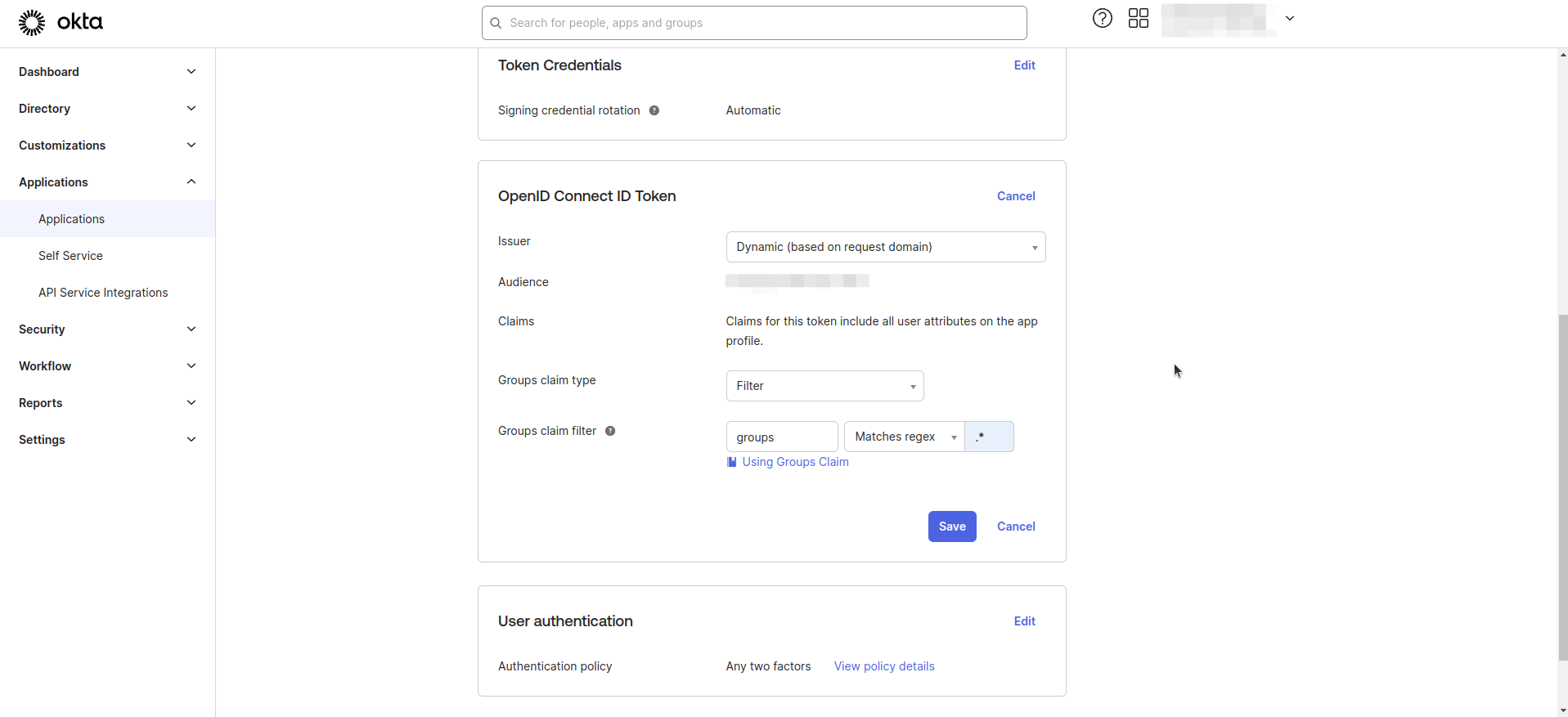
Step 2. Create and Set Role Attribute to User
The roles will be stored in user attributes.
- Navigate to the Directory > Profile Editor section from left navigation menu.
- Select the User (default) from profile list.
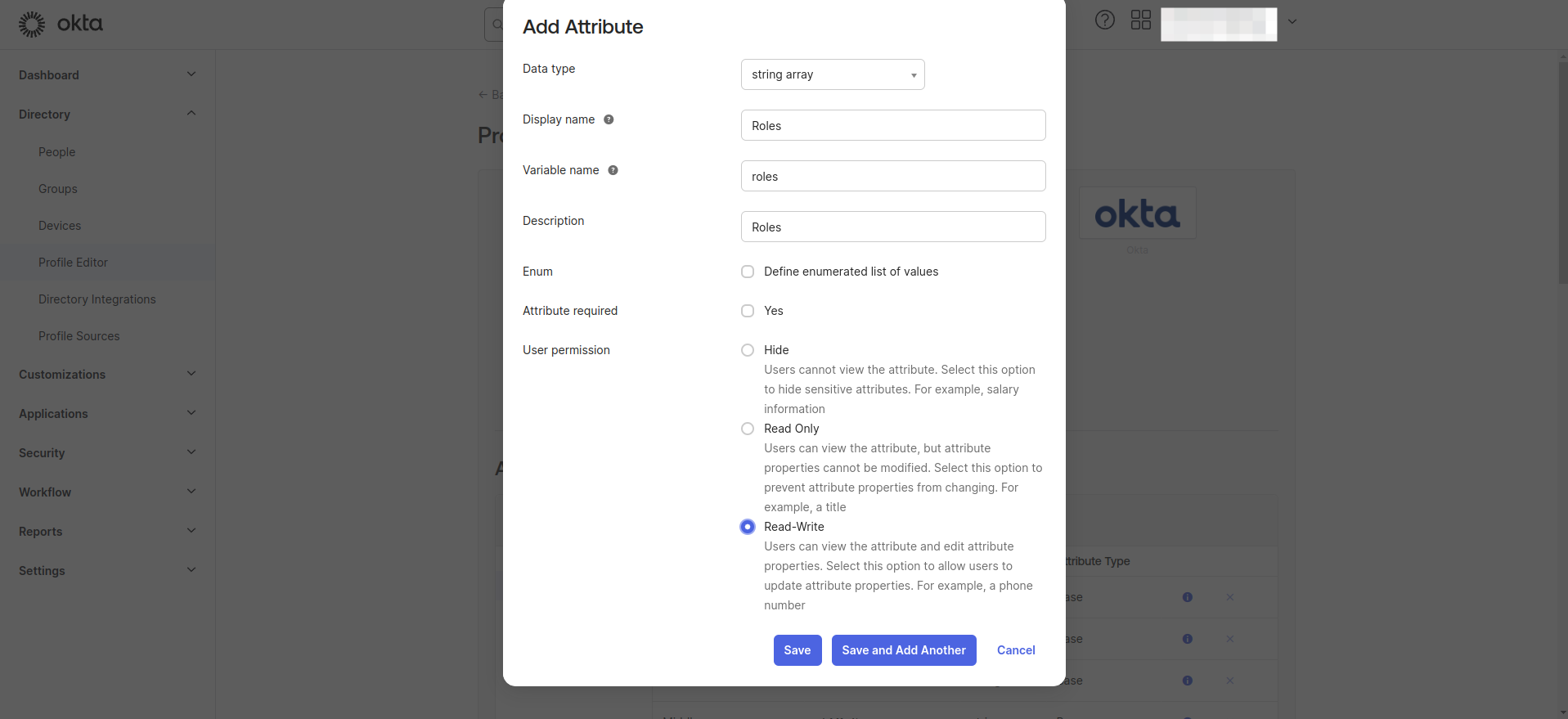
- Click Add Attribute.
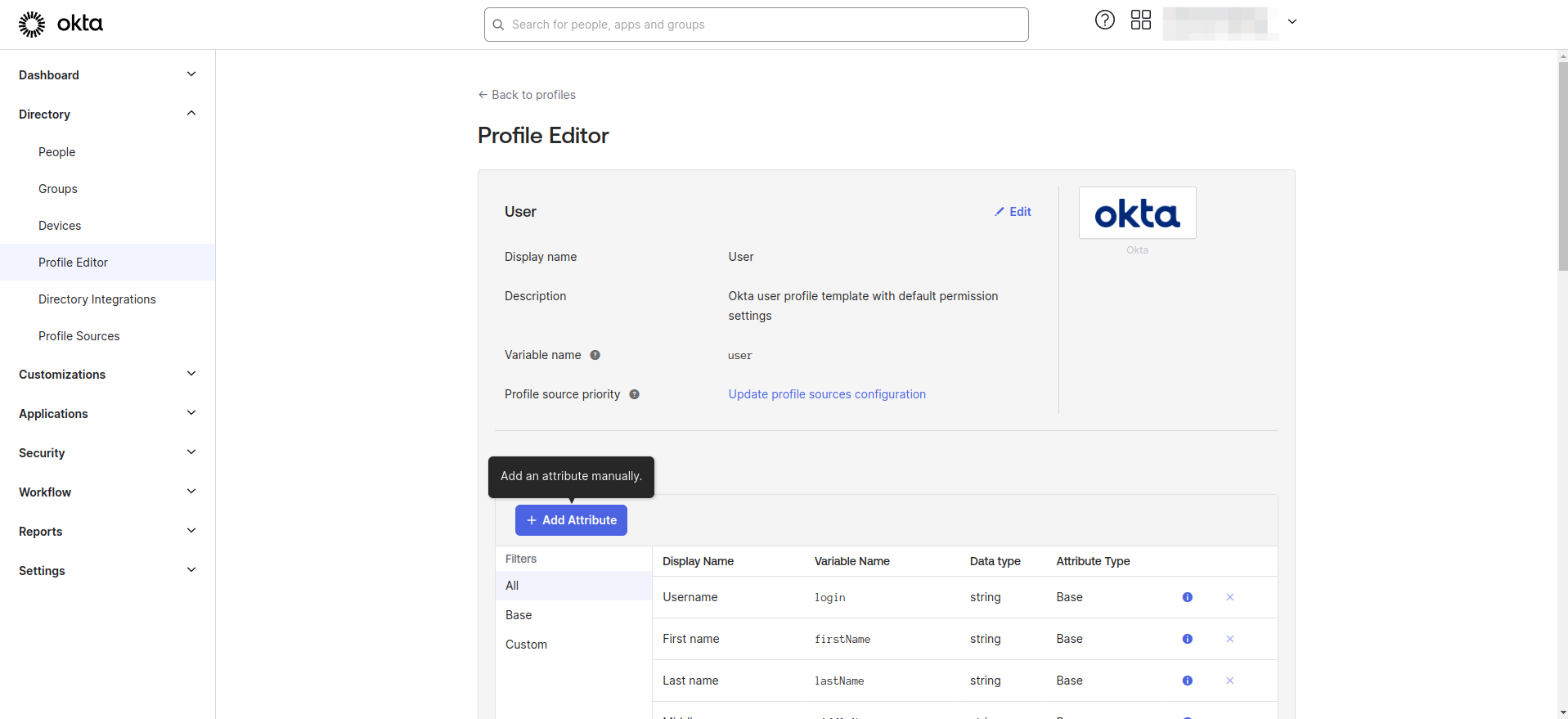
- Add a new user attribute with the following attributes.
- Data type: Choose "String Array"
- Display name: Enter "Roles"
- Variable name: Enter "roles"
- User permission: Choose "Read-Write"
- Navigate to the Directory > Profile Editor section from left navigation menu.
- Select the application-specific user profile named "Your Okta Application Name" User from the profile list.
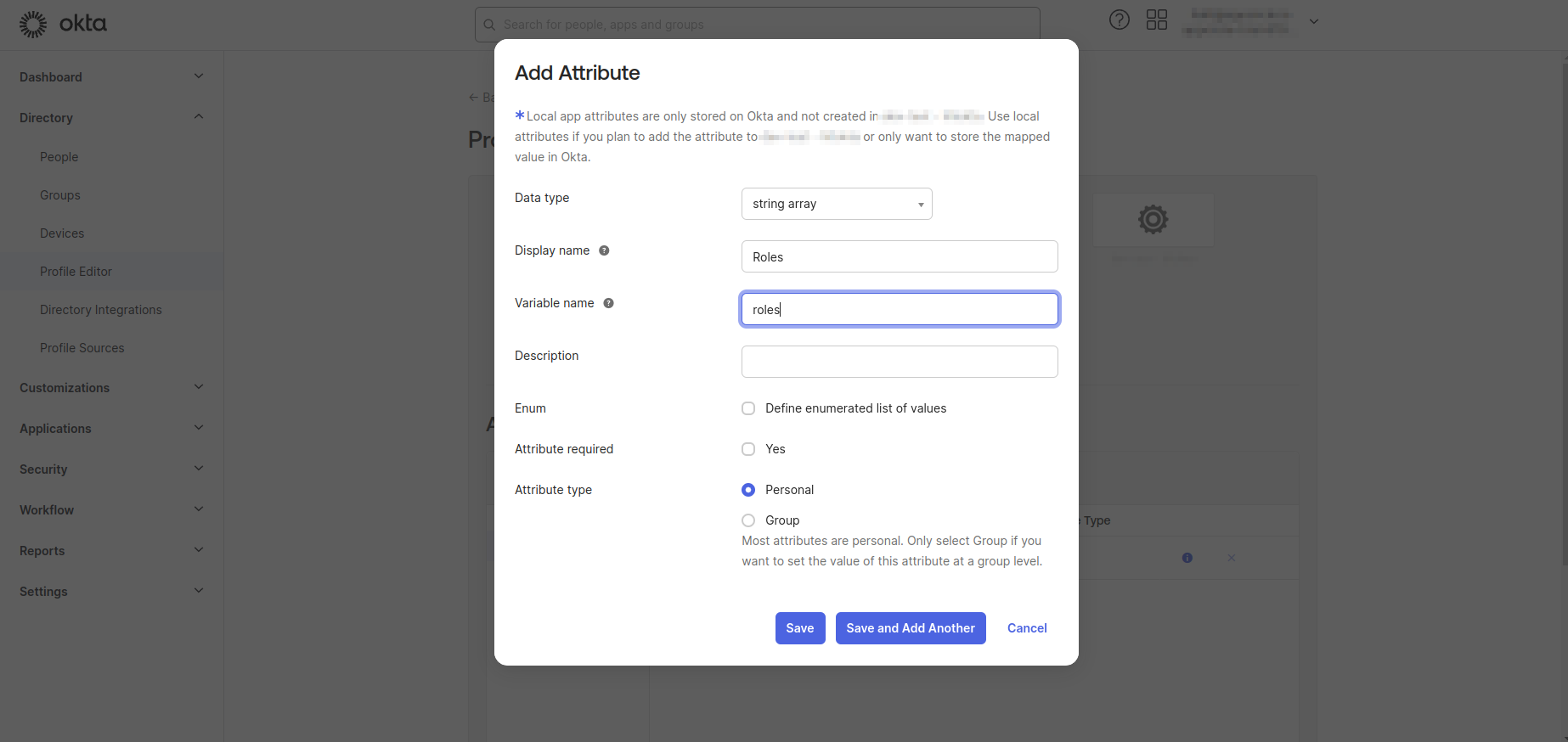
- Click Add Atribute and add new attribute with the following configuration. Then click Save.
- Data type: Choose "String Array"
- Display name: Enter "Roles"
- Variable name: Enter "roles"
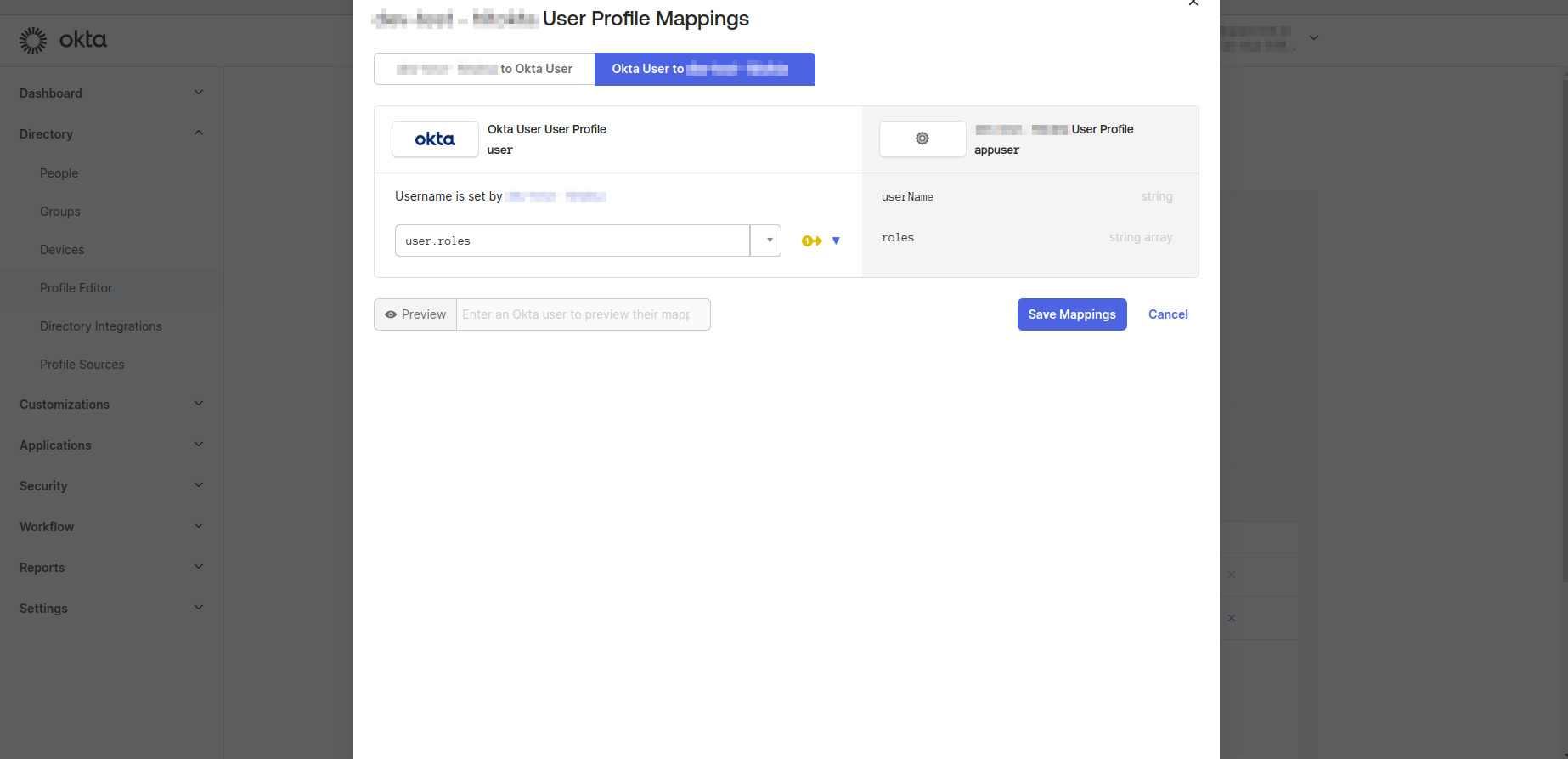
- Click Mappings and switch to Okta User to "Your Application Name" tab. Define a mapping between the user roles attribute and the application user roles attribute as shown in the image below.
- Navigate to the Directory > People section from left navigation menu.
- Select a user from the list.
- Navigate to the Profile tab.
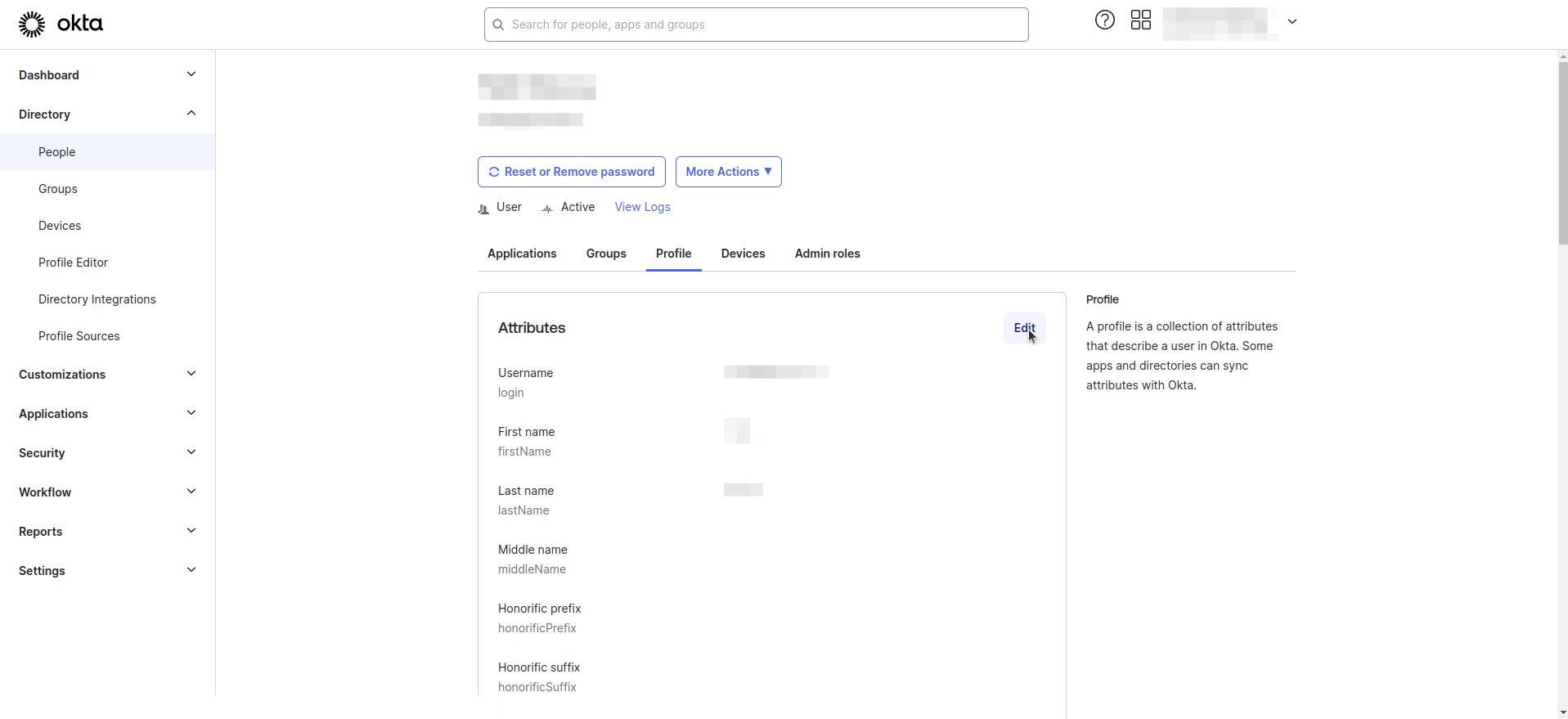
- Click Edit and update the user's role attribute. For example, set it to 'Manager'.
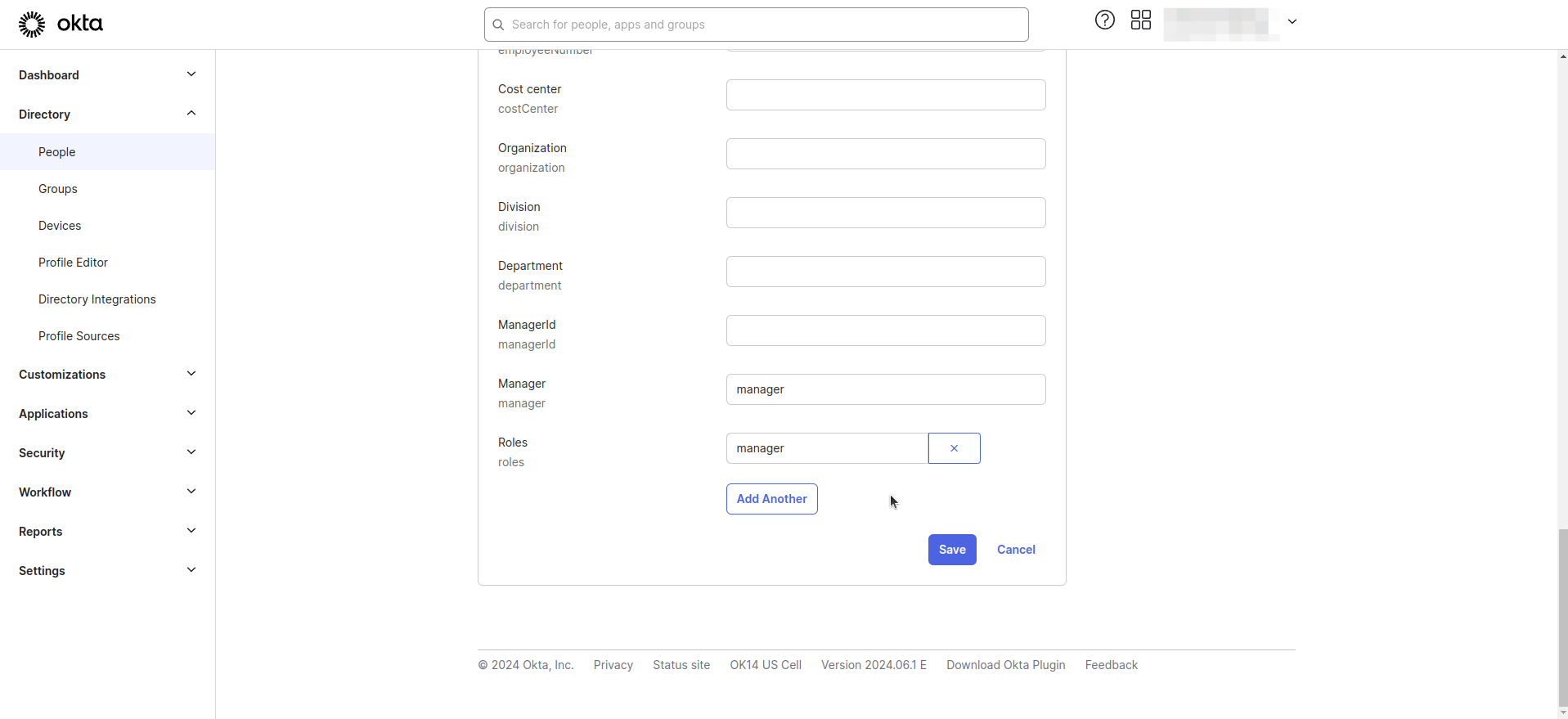
Step 3. Define the Role Claim
- Navigate to the Security > API > Authorization Servers section from left navigation menu.
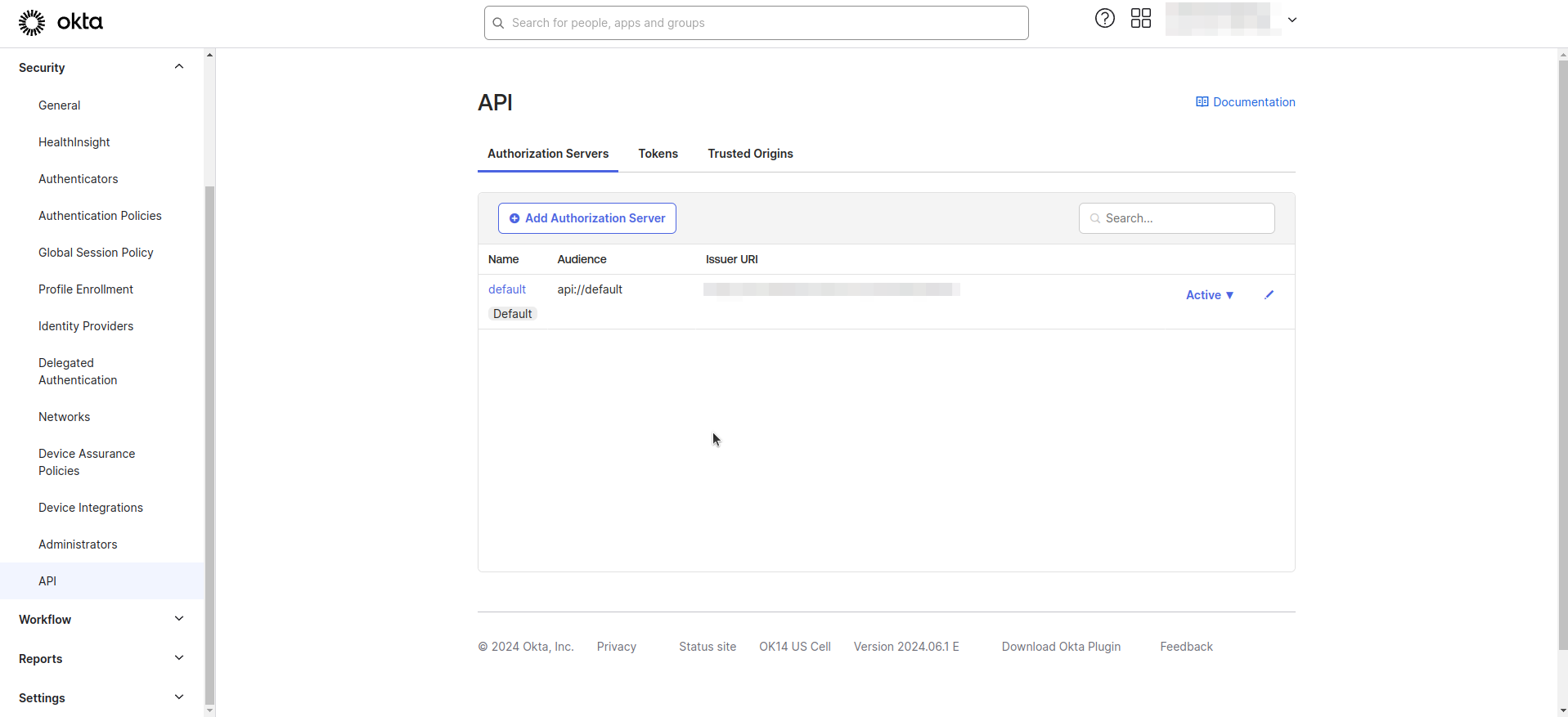
- Click default
- Navigate to the Claims tab.
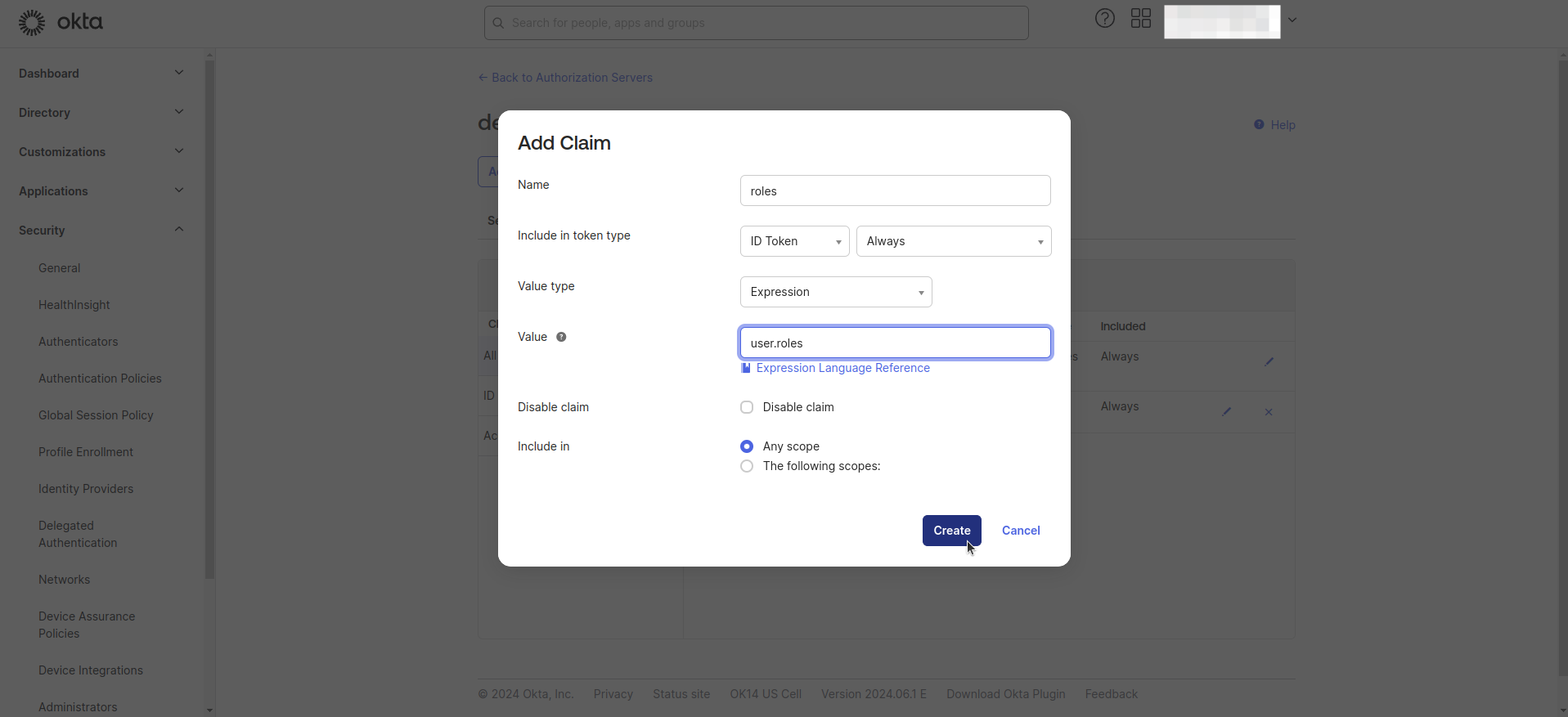
- Add new claim as the following configuration.
- Name: Enter "Roles"
- Include in token type: Select "ID Token" and "Always"
- Value type: Select "Expression"
- Value: Enter "user.roles"
- Disable claim: Select "false"
- Include in: Select "Any scope"
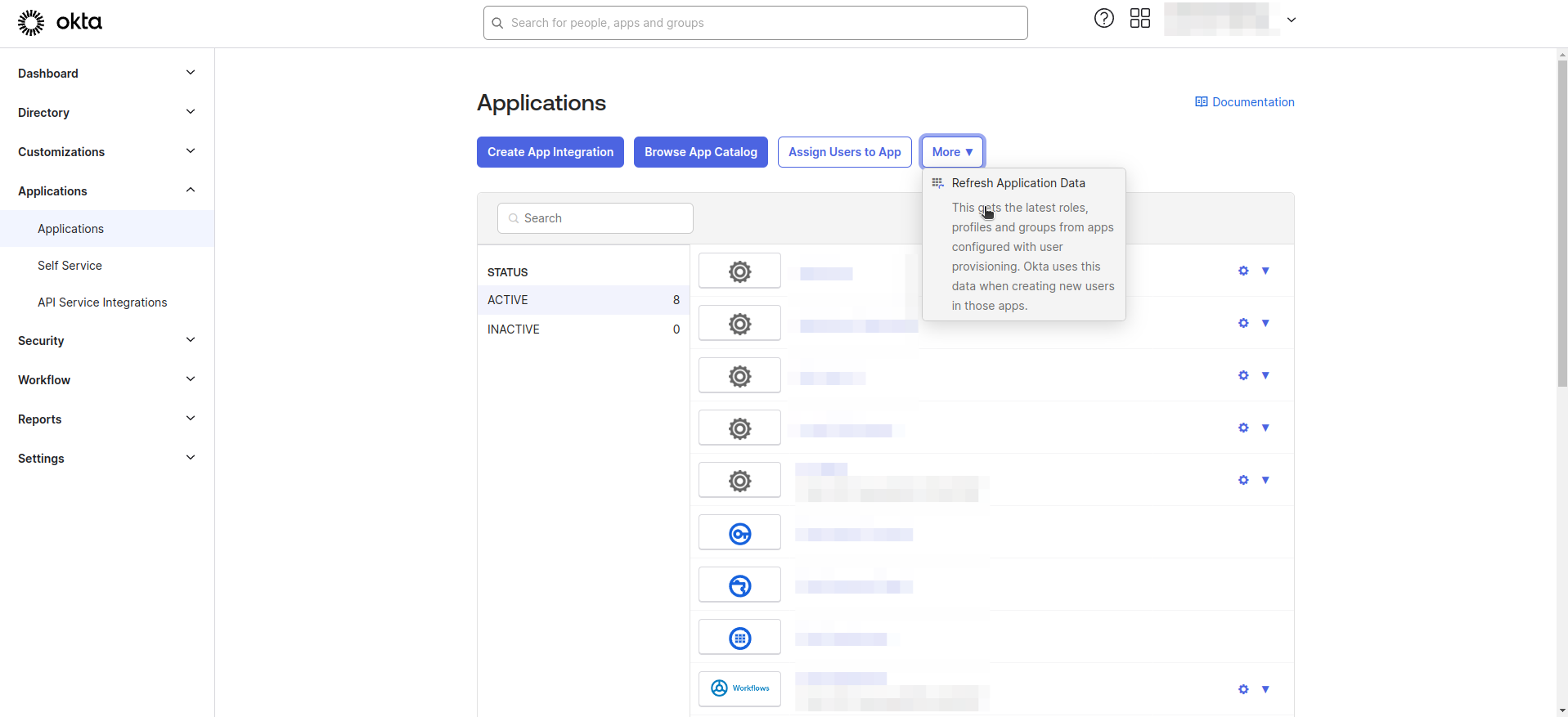
- Navigate to the Applications > Applications section from left navigation menu.
- Click Refresh Application Data.
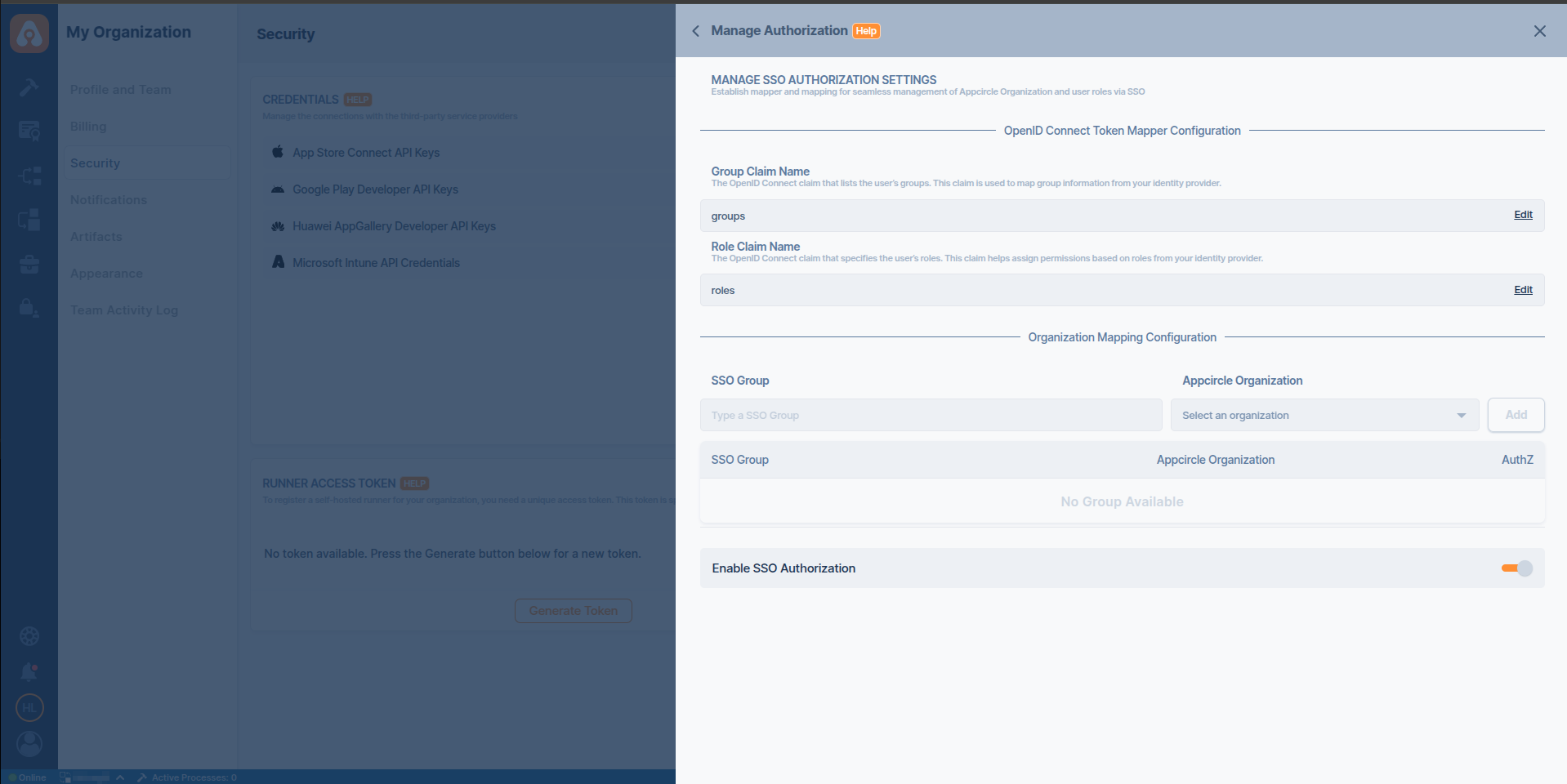
Step 4. Define Group and Role Claim in Appcircle
- Navigate to the Set up OpenID SSO Provider screen in Appcircle, which you accessed during the SSO setup in the "General Configuration Steps."
- Enter Group Attribute Name as
groupsand Role Attribute Name asroles.
Okta (SAML)
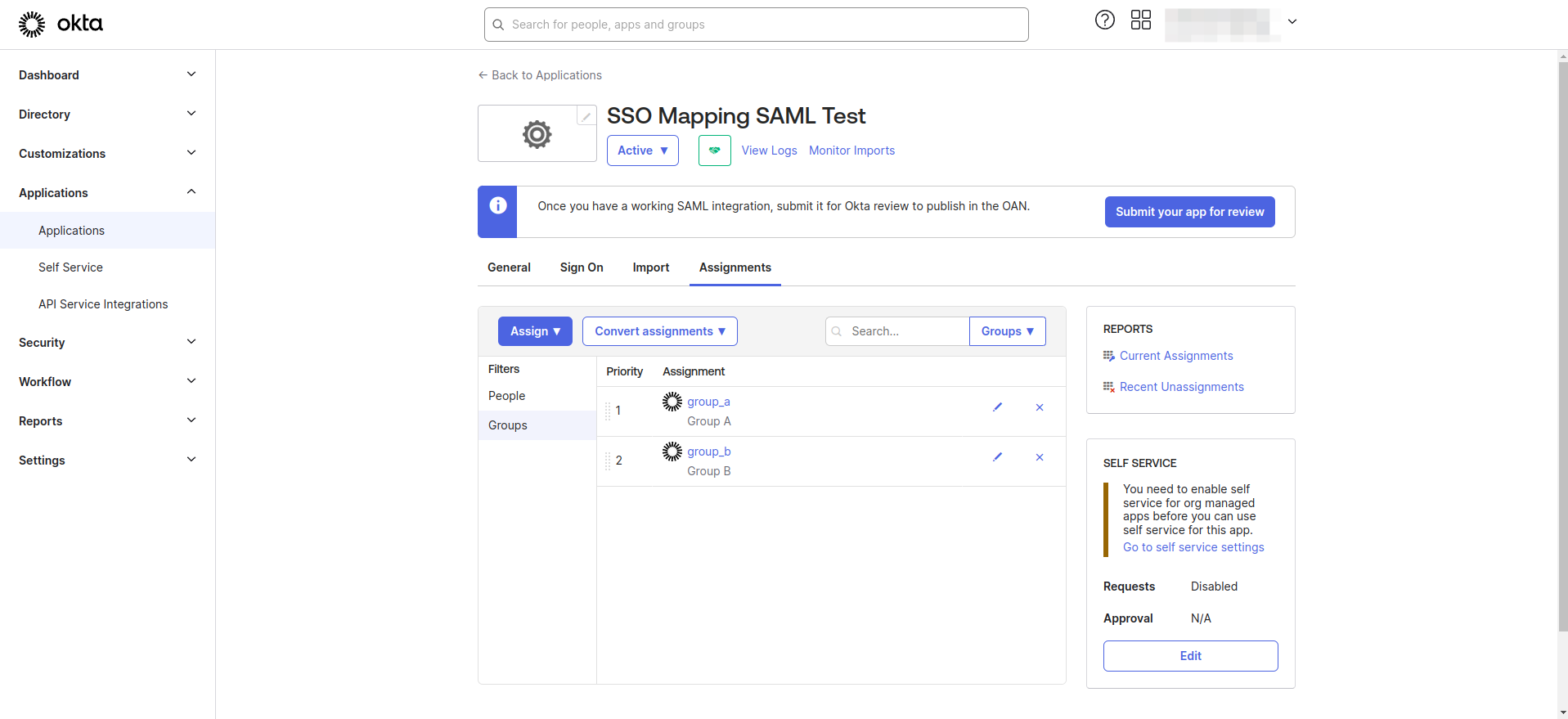
Step 1. Create Groups and Assign to the Application
- Navigate to the Directory > Groups section in the Okta Dashboard. Create the groups as needed.

- Assign users to groups.

- Navigate to the Applications > Applications section from left navigation menu.
- Select your application from the list
- Navigate to the Assignments tab.
- Assign the previously created groups to the application.
Step 2. Create and Set Role Attribute to User
The roles will be stored in user attributes.
- Navigate to the Directory > Profile Editor section from left navigation menu.
- Select the User (default) from profile list.

- Click Add Attribute.

- Add a new user attribute with the following configuration.
- Data type: Choose "String Array"
- Display name: Enter "Roles"
- Variable name: Enter "roles"
- User permission: Choose "Read-Write"

- Navigate to the Directory > Profile Editor section from left navigation menu.

- Select the application-specific user profile named "Your Okta Application Name" User from the profile list.

- Click Add Atribute and add new attribute with the following configuration. Then click Save.
- Data type: Choose "String Array"
- Display name: Enter "Roles"
- Variable name: Enter "roles"

- Click Mappings and switch to Okta User to "Your Application Name" tab. Define a mapping between the user roles attribute and the application user roles attribute as shown in the image below.

- Navigate to the Directory > People section from left navigation menu.
- Select a user from the list.
- Navigate to the Profile tab.

- Click Edit and update the user's role attribute. For example, set it to 'Manager'.

Step 3. Define Group and Role Attributes
- Navigate to the Applications > Applications section.
- Select your application from the list and navigate to the General tab.
- Click on Edit in SAML Settings
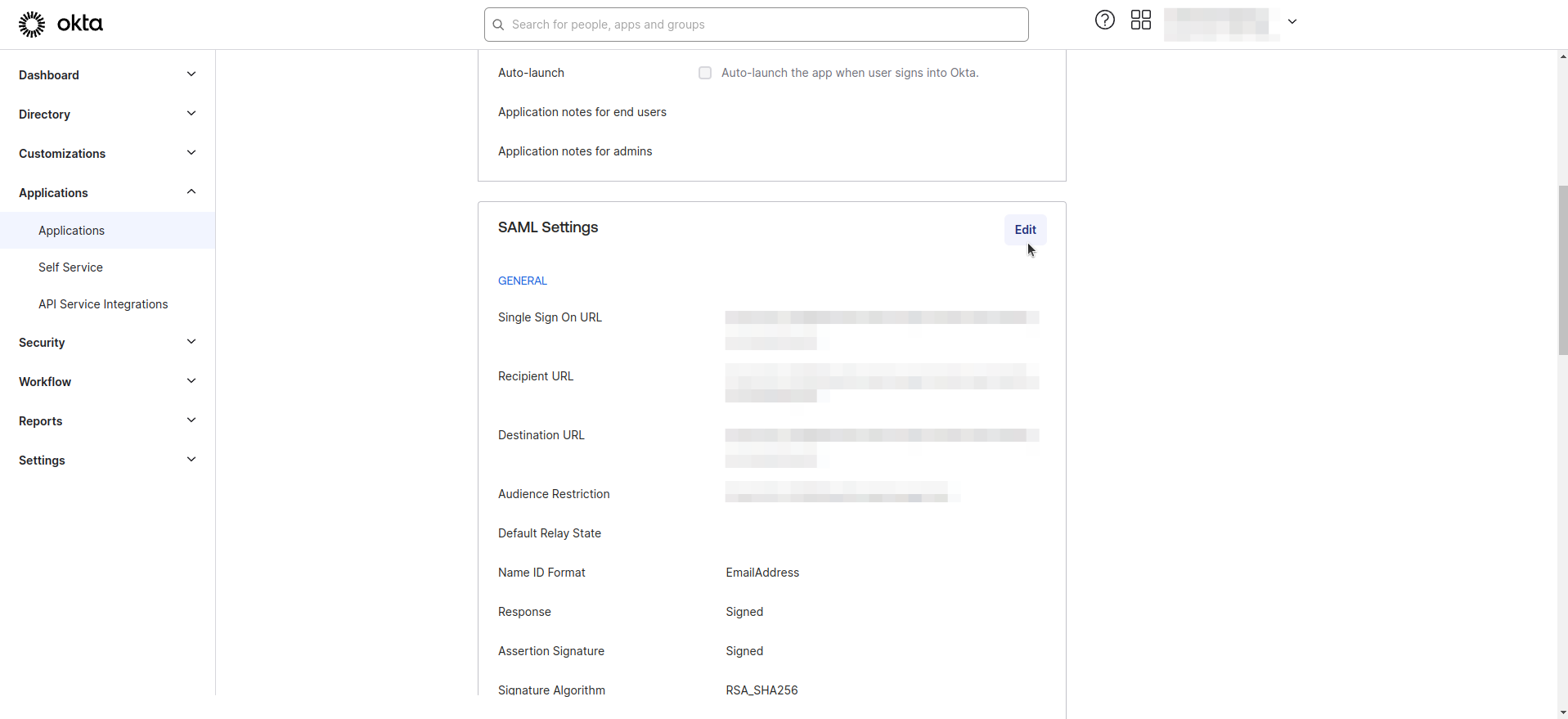
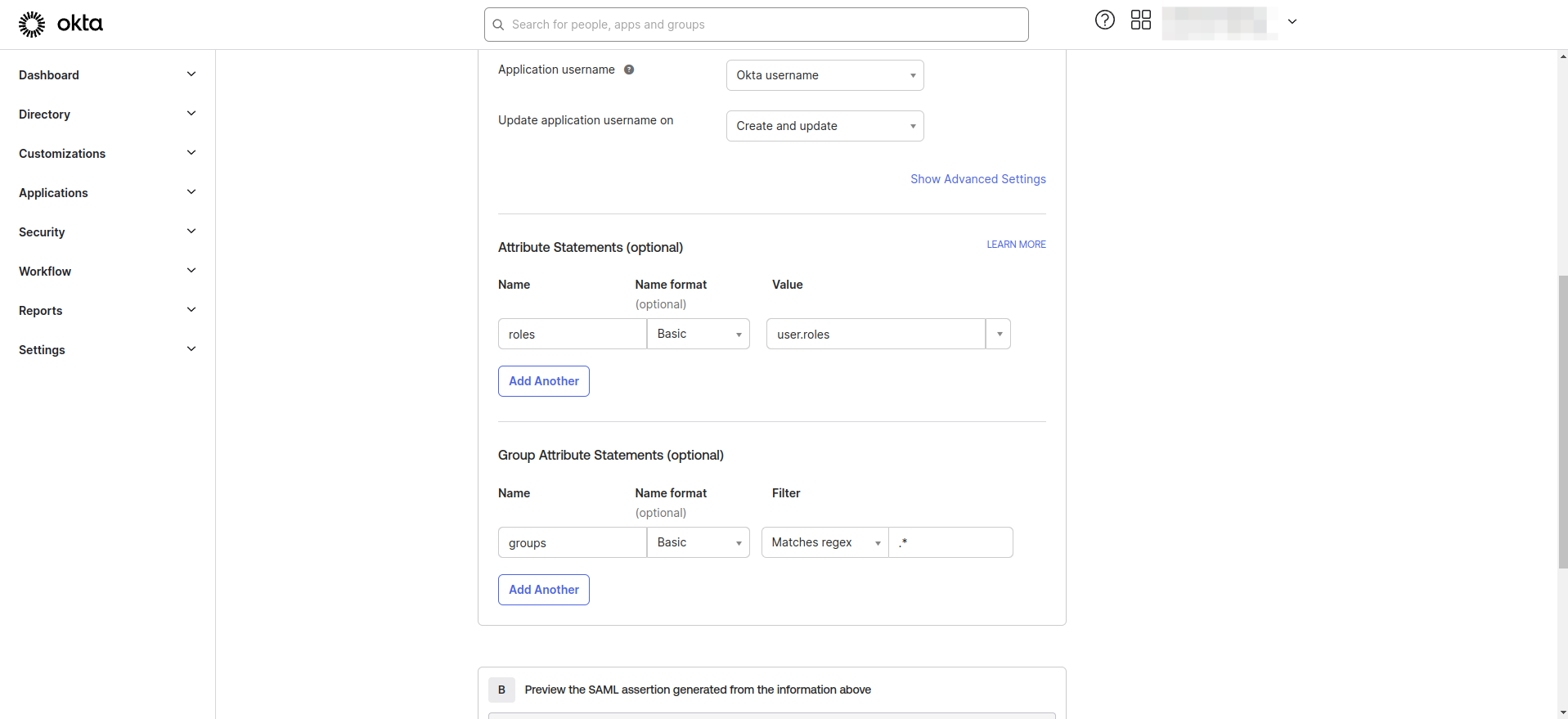
- Enter the Group and Role Attribute statement as following configuration.
Add attribute statement as below
- Name: Enter "roles"
- Name format: Select "Basic"
- Value: Enter "user.roles"
Add group attribute statement as below
- Name: Enter "groups"
- Name format: Select "Basic"
- Filter: Select "Matches regex"
- Filter Value: Enter ".*"
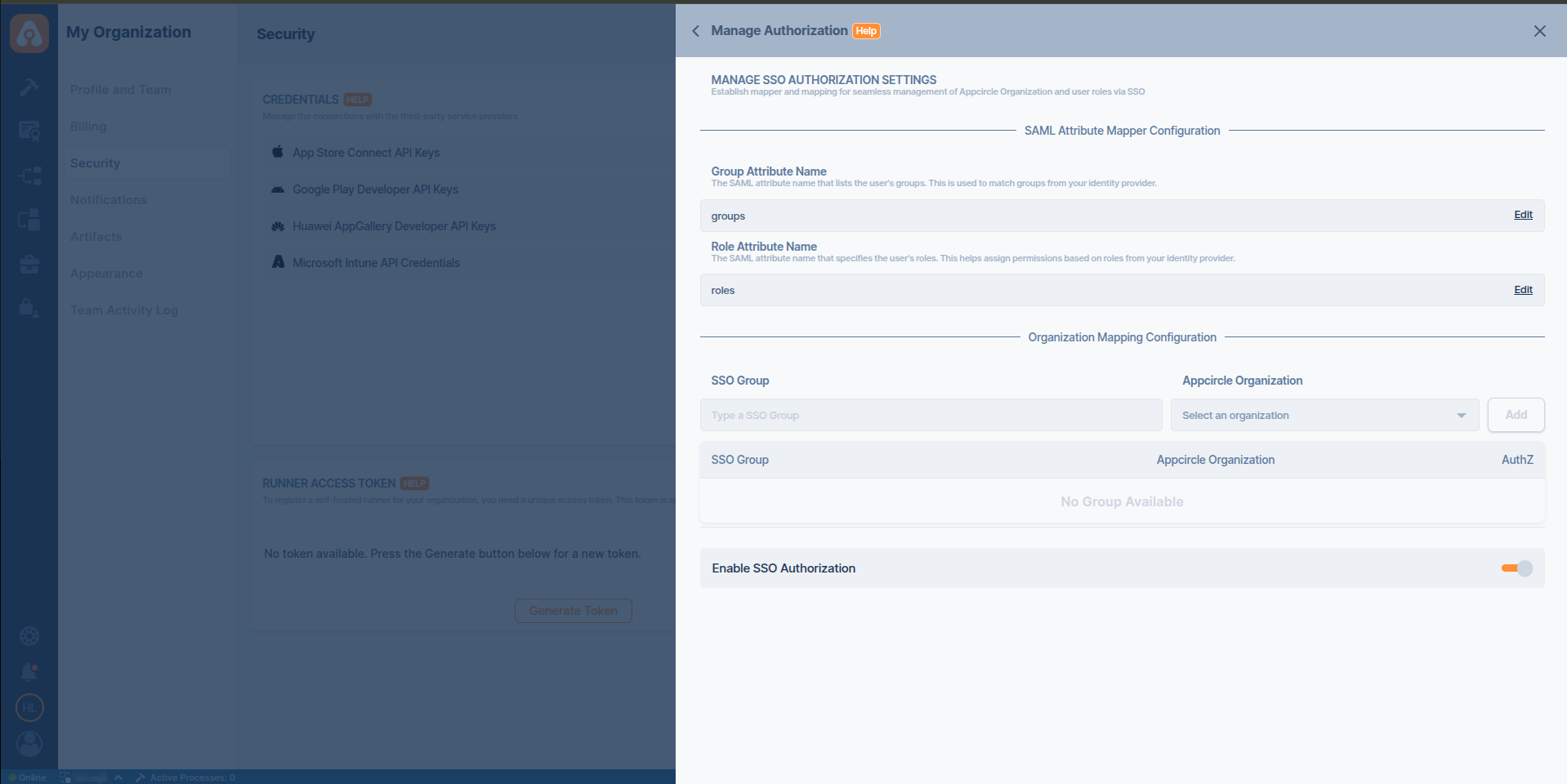
Step 4. Define Group and Role Claim in Appcircle
- Navigate to the Set up OpenID SSO Provider screen in Appcircle, which you accessed during the SSO setup in the "General Configuration Steps."
- Enter Group Attribute Name as
groupsand Role Attribute Name asroles.
4. Testing and Verification
After configuring SSO Mapping, it is important to test the integration to ensure that users have the correct permissions based on their roles and groups. This section covers how to test the integration.
When a user logs into Appcircle, their organization membership and roles are updated according to the configured Group and Role Mapping.
- Open an incognito window in your browser to avoid any cached sessions interfering with the test.
- Use SSO to log in to Appcircle with a test account.
- Verify if the user's organization membership and roles are updated according to the configured Group and Role Mapping.
In self-hosted deployments, the organization memberships and roles of admin users do not change with SSO authorization; they will remain the same.
Organizations must have at least one owner. After processing SSO Authorization Mapping, if there are no remaining owners in the organization, the user's role and organization membership will remain unchanged for that organization.
5. Limitations
Due to technical limitations, SSO mapping does not support automatic synchronization. Changes such as the removal of a user from the Identity Provider or updates to their groups or roles will only take effect when the user logs in to Appcircle.